The insidious spread of Kimwolf is primarily attributed to its exploitation of residential proxy services, which are marketed as tools for anonymizing and localizing web traffic. However, the malware, often bundled with dubious mobile apps, games, and unofficial Android TV boxes, transforms these end-user devices into proxy nodes. The security firm Synthient, led by Benjamin Brundage, a student at the Rochester Institute of Technology, has been at the forefront of tracking Kimwolf’s explosive growth. Brundage identified a critical flaw in how many residential proxy services operate: they fail to adequately prevent customers from "going upstream" into the local networks of proxy endpoints. This is achieved by attackers manipulating Domain Name System (DNS) settings to target private IP address ranges (RFC-1918), such as 10.0.0.0/8, 192.168.0.0/16, and 172.16.0.0/12, which are commonly used in home and office networks. Brundage’s research revealed that attackers could leverage this vulnerability to send crafted requests and drop malware directly onto devices within these local networks.

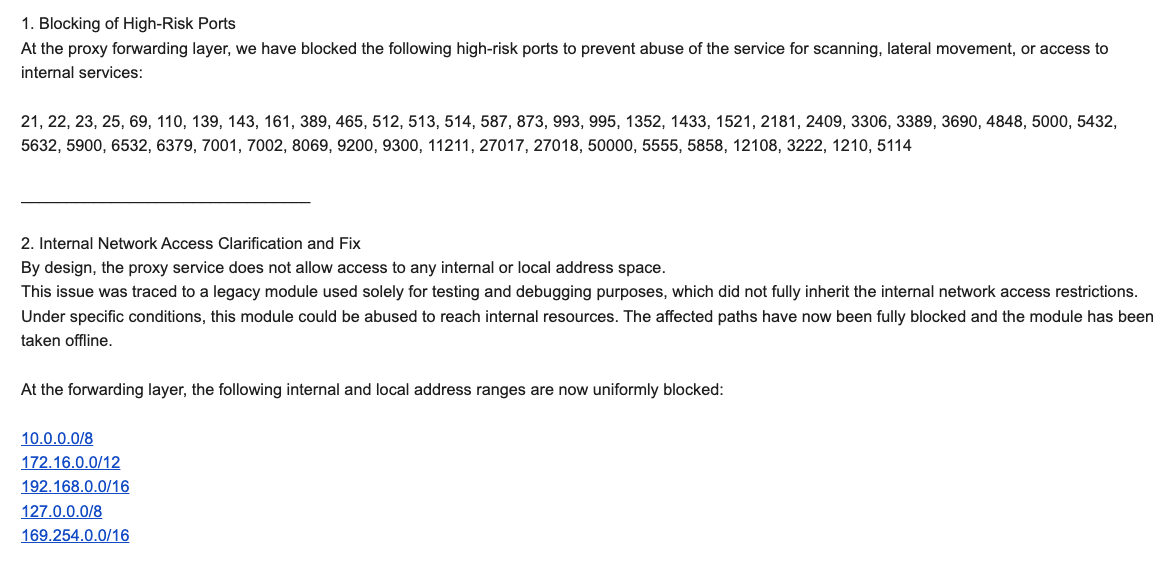
A significant contributing factor to Kimwolf’s rapid spread is the widespread use of Android Debug Bridge (ADB) mode, a powerful diagnostic tool, enabled by default on many unofficial Android TV boxes. This feature, intended for factory use, allows for remote configuration and firmware updates, but when left enabled, it creates a security nightmare by constantly listening for and accepting unauthenticated connection requests. By simply issuing an "adb connect" command with a vulnerable device’s local IP address, attackers gain unrestricted administrative access. Synthient observed a direct correlation between new Kimwolf infections and proxy IP addresses offered for rent by IPIDEA, identified as the world’s largest residential proxy network. Kimwolf has demonstrated an alarming ability to rapidly rebuild itself by tunneling through IPIDEA’s proxy pool, growing from near zero to two million infected systems within days after takedown attempts.
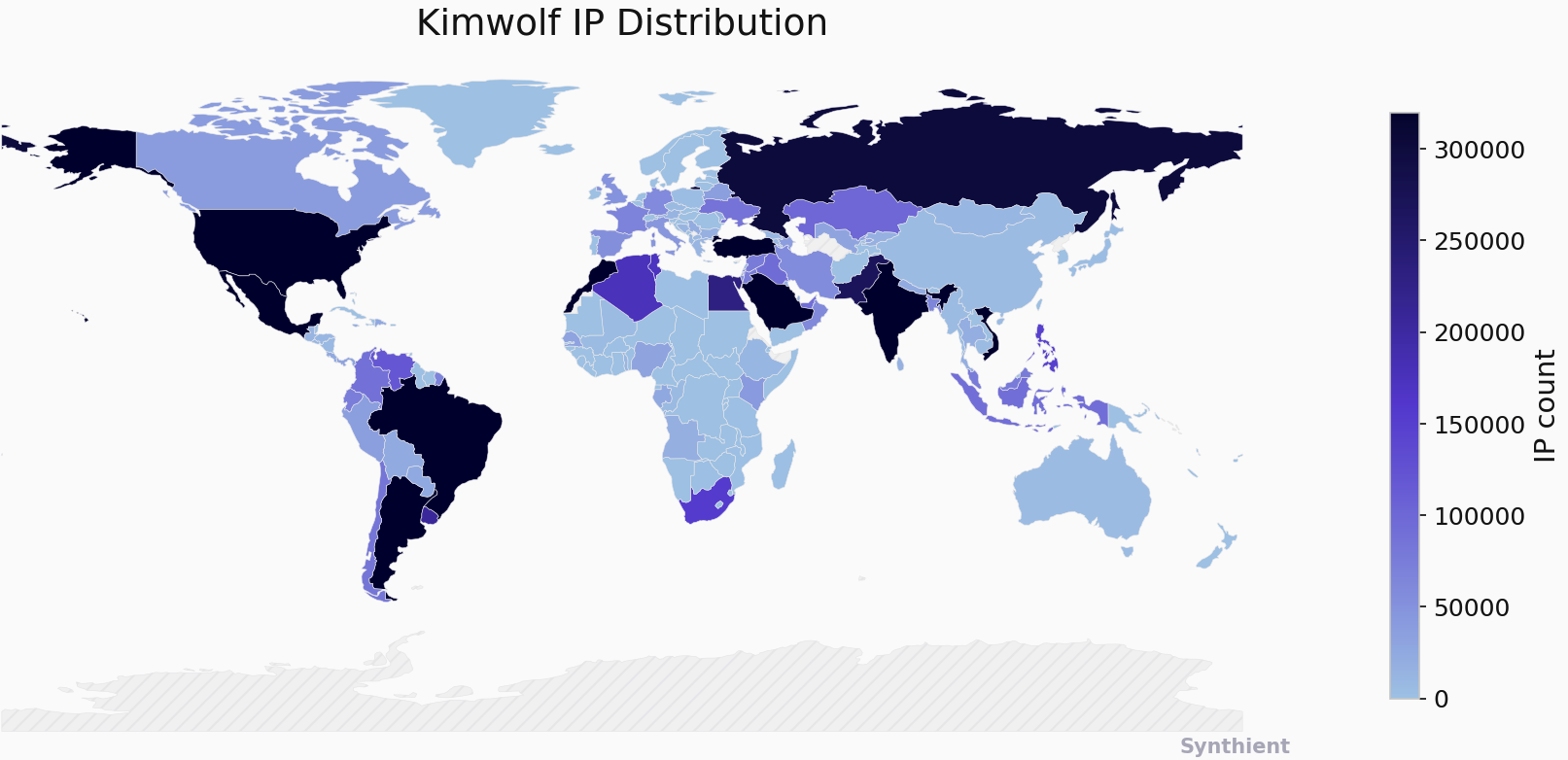
The Chinese security firm XLab also played a crucial role in chronicling Kimwolf’s emergence, initially tracking it as an Android-based variant of the Aisuru botnet. XLab’s analysis indicates that Kimwolf has enslaved between 1.8 and 2 million devices, with significant concentrations in Brazil, India, the United States, and Argentina. The firm noted that the true scale of infected devices is difficult to measure accurately due to the dynamic nature of IP addresses in residential networks and the fact that not all infected devices are online simultaneously. XLab also pointed out the malware’s operators’ peculiar fixation on the author of the original report, embedding "easter eggs" related to their name within the botnet’s code and communications.
The practical implications of Kimwolf are far-reaching and deeply concerning for the average user. The scenario of a guest gaining Wi-Fi access, inadvertently introducing a proxy-infected device, and subsequently compromising other devices on the local network, like an Android TV box or a digital photo frame, highlights the breakdown of traditional network security assumptions. Furthermore, the possibility of attackers modifying router settings to point to malicious DNS servers echoes historical threats like the DNSChanger malware, demonstrating how easily the internet’s navigation system can be subverted.
Compounding the problem, many of these infected devices, particularly unofficial Android TV boxes, bear the ominous disclaimer "Made in China. Overseas use only." These devices are often marketed for free streaming of subscription content, a tempting offer that masks the severe security risks. The lack of built-in security and authentication on these microcomputer boards makes them prime targets. Brundage’s research has led to the compilation of a list of unofficial Android TV boxes most represented in the Kimwolf botnet, urging users to remove such devices from their networks.
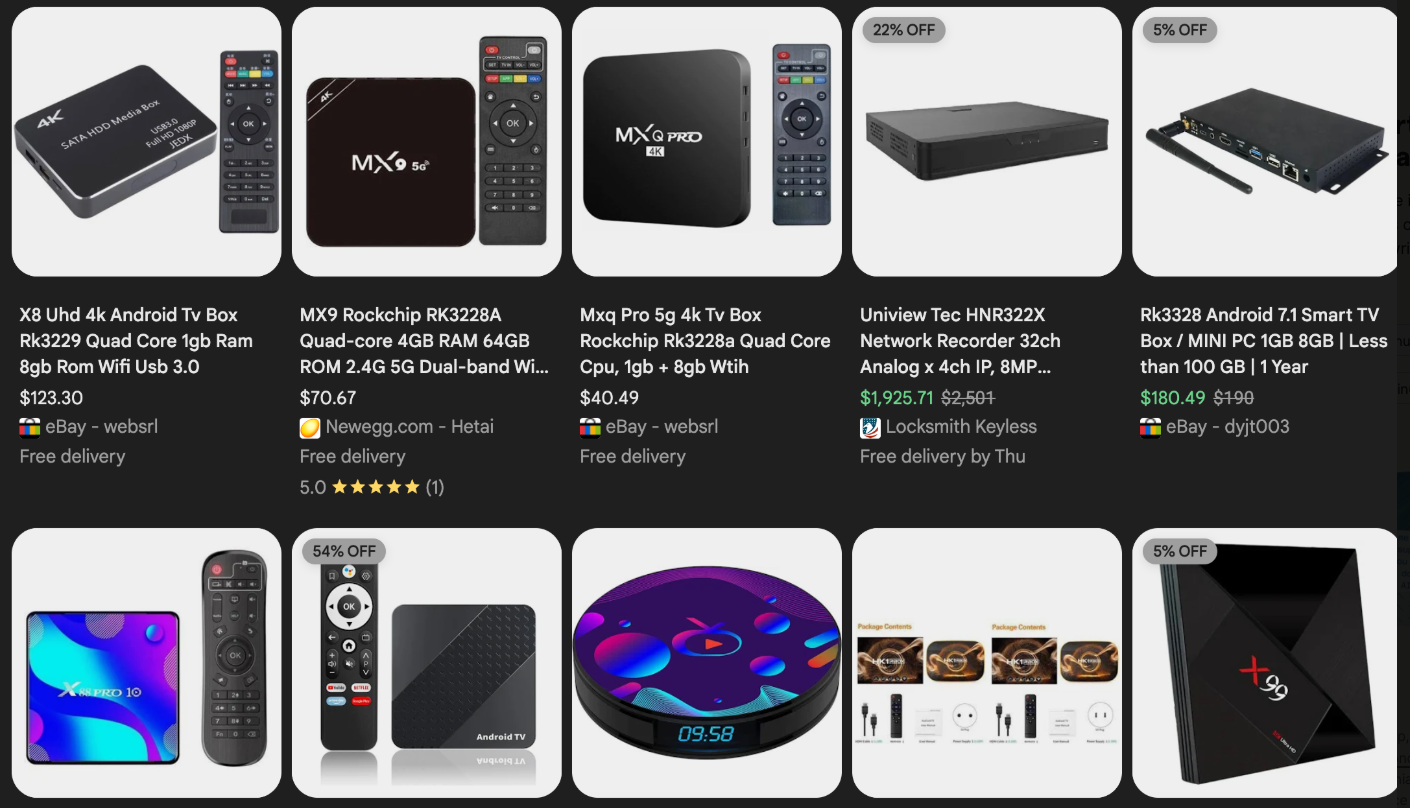
Experts like Chad Seaman of Akamai Technologies emphasize the outdated nature of the assumption that local area networks (LANs) are inherently safe. He stresses the need for consumers to be highly wary of unofficial Android TV boxes and residential proxy schemes, as the security model where LANs are considered impenetrable is no longer valid. Seaman notes that the infection vector is not limited to Android devices, with proxy services offering SDKs for Mac, Windows, and iPhones, meaning any device connected to a network could potentially be compromised.
This issue is further underscored by Google’s lawsuit against "BadBox 2.0 Enterprise," a botnet of over ten million unsanctioned Android streaming devices involved in advertising fraud, and an FBI advisory warning of cybercriminals gaining unauthorized access to home networks through pre-configured malware or malicious app downloads during setup. Lindsay Kaye of HUMAN Security, a company involved in BADBOX investigations, highlights that these botnets and proxy networks facilitate a wide range of illicit activities, including advertising fraud, ticket scalping, retail fraud, account takeovers, and content scraping. Kaye advises consumers to stick to reputable brands and be cautious of "free" or "too good to be true" offers, as well as the apps they install.
The use of a "Guest" Wi-Fi network is recommended as a measure to isolate guests’ devices from the local network, preventing them from accessing shared resources or potentially spreading malware. While a pro-piracy camp dismisses these security concerns, arguing that even factory-infected devices can be re-flashed, the reality is that most consumers purchasing these devices lack the technical expertise for such mitigation. The entertainment industry’s apparent lack of visible pressure on e-commerce vendors to stop selling such insecure and malicious hardware is also a point of concern, as these TV boxes serve as an attractive nuisance for cybercriminals. The investigation into Kimwolf is ongoing, with future parts promising to delve deeper into the individuals and entities that have profited from this widespread threat.