China-based phishing groups, previously notorious for relentless SMS scams involving undelivered packages or unpaid toll fees, are now actively peddling a new, sophisticated offering: phishing kits designed for the mass creation of deceptively authentic e-commerce websites. These kits are engineered to convert stolen customer payment card data into mobile wallets for Apple and Google, coinciding with the peak holiday shopping season. Security experts also note that these same malicious actors are now leveraging SMS lures that promise unclaimed tax refunds and mobile rewards points to ensnare unsuspecting consumers.
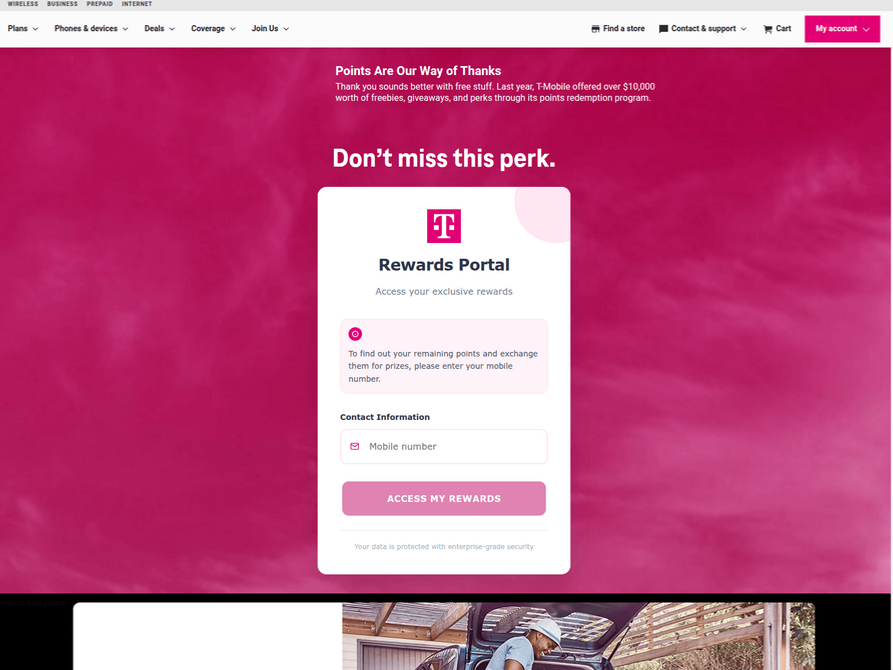
In recent weeks, a surge in domain registrations has been observed for scam websites masquerading as legitimate platforms offering T-Mobile customers the opportunity to claim substantial rewards points. These fraudulent domains are being aggressively promoted through scam messages sent via Apple’s iMessage and Google’s RCS messaging service. The website analysis service urlscan.io has documented the deployment of thousands of such phishing domains in a remarkably short period. These deceptive websites are specifically designed to load only when accessed from a mobile device, subsequently requesting visitors’ personal information, including their name, address, phone number, and crucially, payment card details, under the guise of claiming these supposed rewards.
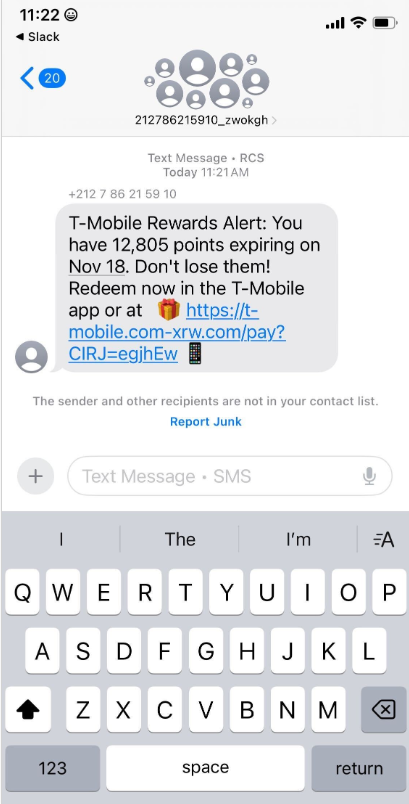
Once a victim submits their card information, the phishing site prompts them to share a one-time code sent via SMS by their financial institution. This code, intended for legitimate transaction verification, is actually sent because the fraudsters are attempting to enroll the victim’s compromised card details into an Apple or Google mobile wallet. If the victim provides this one-time code, the phishers gain the ability to link the victim’s card to a mobile device under their physical control.
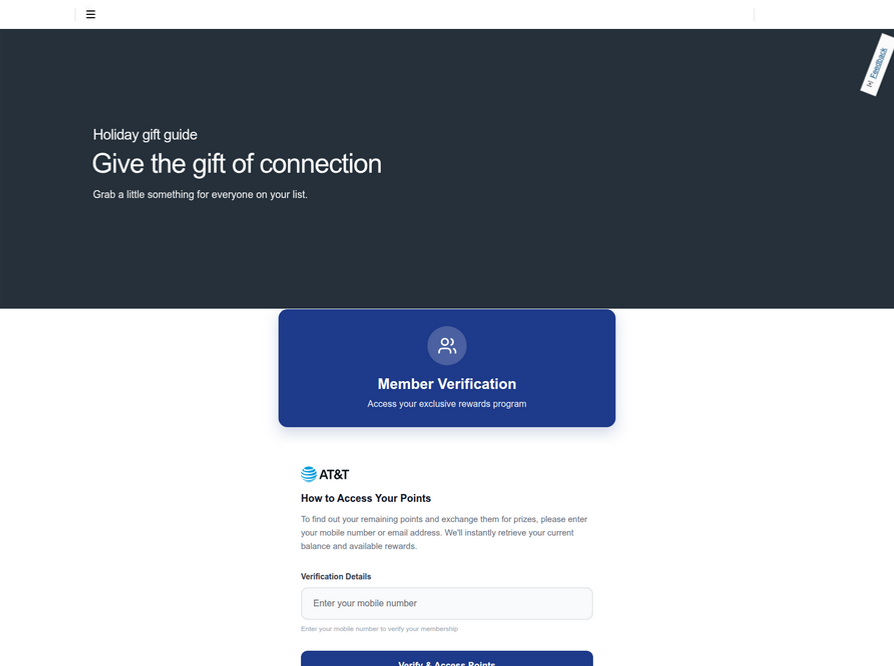
Further investigation by pivoting off these T-Mobile phishing domains reveals a similar scam targeting AT&T customers, employing identical tactics. Ford Merrill, a security researcher at SecAlliance, a CSIS Security Group company, explains that while these mobile points redemption schemes have been prevalent in other regions like the EU and Asia for some time, they have only recently been widely deployed against U.S. consumers. These sophisticated phishing-as-a-service platforms, sold by multiple China-based cybercriminal groups, are now being adapted to exploit U.S. users.
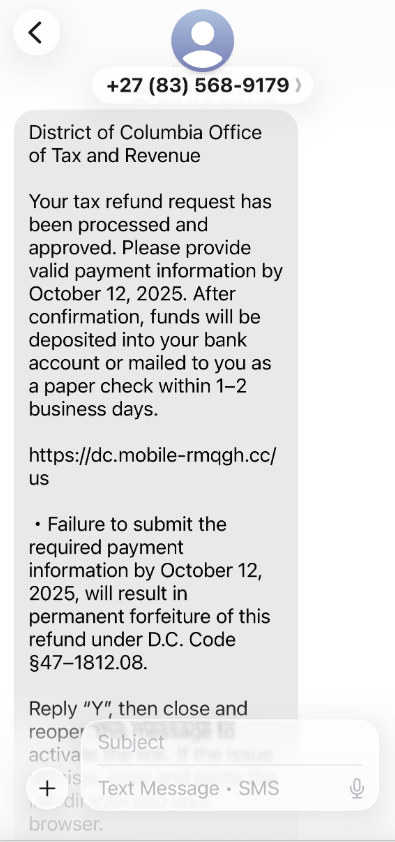
A review of other domains linked to this Chinese SMS phishing syndicate also shows a disturbing trend of spoofing U.S. state tax authorities. Recipients are being informed of unclaimed tax refunds, with the ultimate goal being to phish for payment card information and the critical one-time verification codes. For instance, a scam message impersonating the District of Columbia’s Office of Tax and Revenue has been observed, employing the same deceptive methodology.
While many SMS phishing (smishing) domains are quickly identified and flagged by browser manufacturers as malicious, one area experiencing significant growth is fake e-commerce shops. These are particularly insidious because they do not rely on mass spamming to attract victims, making them harder to detect. The same Chinese phishing kits used for package redelivery scams are equipped with modules that allow for the rapid deployment of convincing fake online storefronts. These fraudulent stores are often advertised on platforms like Google and Facebook, and consumers typically encounter them while searching for deals on specific products.
In these fake e-commerce scenarios, customers willingly provide their payment card and personal information during the checkout process. The scam culminates in a request for a one-time code from their financial institution, falsely claimed to be for transaction verification. In reality, this code is required by the scammers to finalize the enrollment of the phished card data into a mobile wallet. These fake shops typically fetch the malicious code that exposes them as fraudulent only during the checkout process, making them challenging to discover through broad web scanning. Furthermore, many customers only realize they have been defrauded weeks later when their purchased items fail to arrive. Merrill highlights that these fake e-commerce sites can operate undetected for months, evading detection by safe browsing tools.
Fortunately, reporting these SMS phishing lures and websites is a crucial step in their takedown. Raymond Dijkxhoorn, CEO of SURBL, a widely used blocklist for malicious domains and IP addresses, has launched smishreport.com. This website allows users to upload screenshots of any smishing messages they receive, enabling SURBL to identify and block new patterns and related domains. Dijkxhoorn emphasizes that by reporting unlisted domains, they can effectively "kill the rest" of the matching fraudulent sites.
The final weeks of the calendar year typically witness a substantial increase in smishing activity, particularly package redelivery scams impersonating the U.S. Postal Service or commercial shipping companies. Merrill observes that "Every holiday season there is an explosion in smishing activity," attributing this to increased urgency in online shopping, reduced attention spans, and a heightened susceptibility to phishing.
Consumers are urged to approach online shopping with a heightened sense of security, recognizing that opting for the lowest advertised prices can be a risky proposition. Even when shopping at reputable online stores, vigilance is required regarding offers from third-party sellers that may appear too good to be true. For unfamiliar online merchants, especially new ones, investigating their reputation is paramount. A quick WHOIS search on a website’s domain name can reveal its creation date, with newer sites posing a significantly higher risk of being fraudulent.
When receiving messages about order or shipment issues, it is advisable to navigate directly to the e-commerce or shipping website rather than clicking on links or attachments, especially those that create a sense of urgency. Scammers often exploit emergencies to bypass victims’ defenses. Beyond outright scams, inflated shipping and handling fees can offset seemingly attractive product discounts. Consumers should carefully review shipping times, return policies, and watch out for hidden charges during the checkout process.
Crucially, maintaining close scrutiny of monthly financial statements is essential. Fraudsters often use the holiday season’s flurry of transactions to conceal unauthorized charges. Promptly reviewing credit card bills and disputing any unrecognized transactions is vital to mitigating financial losses.