China-based phishing groups, previously known for relentless scam SMS messages about undelivered packages or unpaid tolls, are now aggressively promoting a new threat: sophisticated phishing kits designed to mass-create convincing fake e-commerce websites. These kits, timed perfectly for the holiday shopping season, aim to steal customer payment card data and convert it into mobile wallets from Apple and Google. Security experts also report that these same malicious actors are now leveraging SMS lures promising unclaimed tax refunds and tempting mobile rewards points.
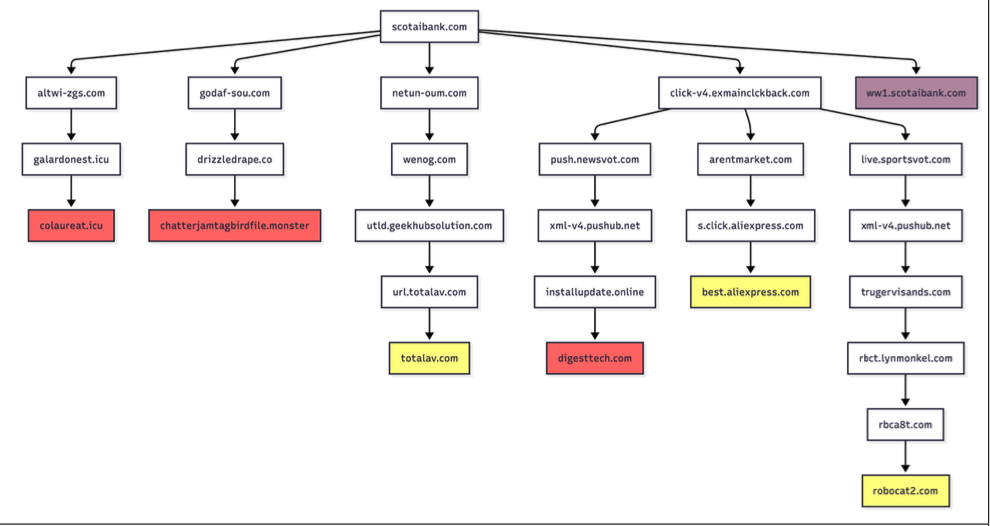
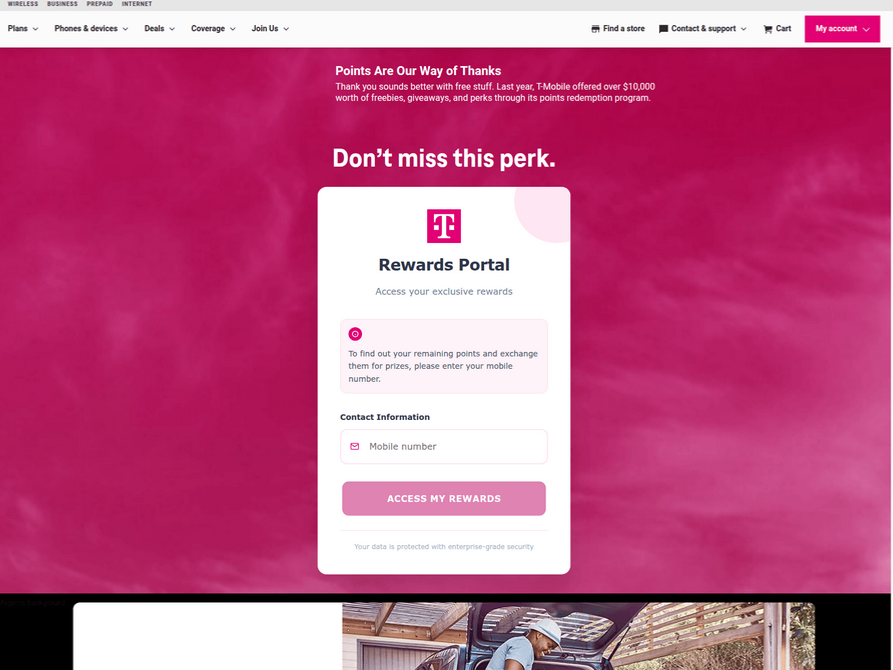
In the past week alone, thousands of domain names have been registered for scam websites masquerading as legitimate offers for T-Mobile customers to claim a substantial number of rewards points. These fraudulent domains are being actively promoted through SMS messages, often delivered via Apple’s iMessage or the functionally equivalent RCS messaging service on Google phones. The website scanning service urlscan.io has documented the rapid deployment of these phishing domains, with thousands appearing in just a few days. Crucially, these phishing websites are engineered to load only when accessed from a mobile device. Upon visiting, users are prompted to provide personal information, including their name, address, phone number, and critically, payment card data, under the guise of claiming these promised points.
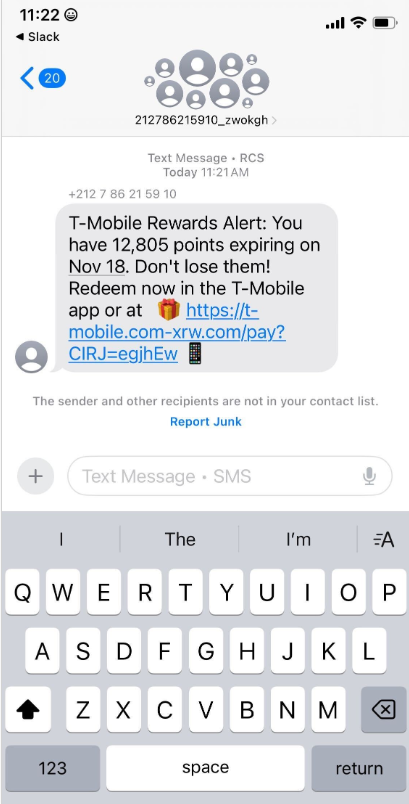
Once a victim submits their card details, the phishing site then deceives them into sharing a one-time code sent via SMS by their financial institution. In reality, this code is being requested because the fraudsters are attempting to enroll the phished card details into a mobile wallet service, such as Apple Pay or Google Pay. If the victim provides this one-time code, the phishers gain the ability to link the victim’s payment card to a mobile device they physically control, enabling fraudulent transactions.
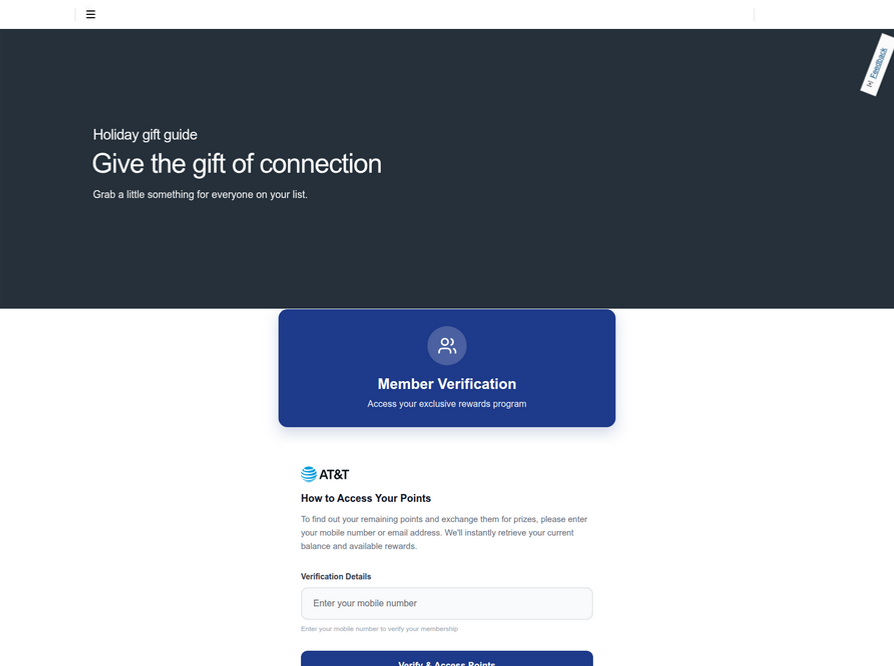
The pivot to these mobile wallet schemes is not limited to one carrier. Further analysis of domains associated with this Chinese SMS phishing syndicate reveals a similar scam targeting AT&T customers, employing the same tactics of promising rewards points. Ford Merrill, a security researcher at SecAlliance, a CSIS Security Group company, explains that while China-based cybercriminal groups have been offering these "phishing-as-a-service" platforms for some time, the mobile points lure has only recently been significantly targeted at U.S. consumers. Merrill notes that these points redemption schemes, while prevalent in regions like the EU and Asia, have historically seen less traction in the U.S.
Beyond mobile rewards, the same syndicate is also spoofing U.S. state tax authorities, sending messages that claim recipients are eligible for an unclaimed tax refund. The objective remains the same: to phish for payment card information and the crucial one-time verification code.
While many SMS phishing or "smishing" domains are quickly flagged by browser makers as malicious, a burgeoning area of concern is the proliferation of fake e-commerce shops. These fraudulent storefronts are more insidious because they do not rely on mass spamming and can be harder to detect. The same Chinese phishing kits that facilitate package redelivery scams are equipped with modules that enable the rapid deployment of convincing, yet entirely fake, online stores. These phony shops are often advertised on platforms like Google and Facebook, luring consumers who are actively searching for deals on specific products.
In these fake e-commerce scenarios, customers willingly provide their payment card and personal information during the checkout process. The scam escalates when the site then requests a one-time code from the user’s financial institution, falsely claiming it’s for transaction verification. In reality, this code is needed by the scammers to immediately enroll the supplied card data into a mobile wallet. The deceptive nature of these fake shops lies in their ability to fetch malicious code only during the checkout process, making them difficult to identify through mass web scanning. Furthermore, many consumers only realize they have been defrauded weeks later when their purchased item fails to arrive. Merrill highlights the challenge, stating, "The fake e-commerce sites are tough because a lot of them can fly under the radar. They can go months without being shut down, they’re hard to discover, and they generally don’t get flagged by safe browsing tools."
Reporting these malicious SMS lures and websites is a critical step in their takedown. Raymond Dijkxhoorn, CEO of SURBL, a widely used blocklist for malicious domains, has spearheaded smishreport.com. This website encourages users to upload screenshots of any smishing messages they receive. Dijkxhoorn explains, "If [a domain is] unlisted, we can find and add the new pattern and kill the rest" of the matching domains. The tool simplifies the reporting process, allowing for swift identification and neutralization of emerging threats.
The final weeks of the calendar year typically witness a significant surge in smishing activity, particularly with package redelivery scams impersonating entities like the U.S. Postal Service or commercial shipping companies. Merrill observes, "Every holiday season there is an explosion in smishing activity. Everyone is in a bigger hurry, frantically shopping online, paying less attention than they should, and they’re just in a better mindset to get phished."
Shopping Online Like a Security Pro
Adopting a shopping strategy solely based on the lowest advertised prices can be akin to playing Russian Roulette with one’s finances. Even shoppers who primarily frequent well-known online retailers can fall victim to scams, especially when dealing with third-party sellers on these platforms. It is imperative to investigate the reputation of unfamiliar online merchants. For brand-new e-commerce sites offering suspiciously low prices on popular gadgets, the risk of being scammed increases significantly. A basic WHOIS search on the site’s domain name can offer a quick indication of its lifespan; a more recent "created" date suggests a higher probability of a phantom store.
When encountering messages about order or shipment issues, it is crucial to navigate directly to the e-commerce or shipping website rather than clicking on links or attachments within the message. Phishers and malware distributors often exploit urgent or alarming scenarios to create a false sense of emergency, prompting recipients to lower their guard. Beyond outright scams, be aware that excessively steep discounts may be offset by inflated shipping and handling fees. Scrutinize shipping times, understand return policies, watch for hidden surcharges, and exercise caution when clicking "ok" during the checkout process.
Most importantly, maintain vigilant oversight of monthly financial statements. Fraudsters often exploit the holiday season to inject unauthorized charges onto stolen cards, hoping these bogus purchases will be lost amidst a flurry of legitimate transactions. Therefore, a thorough review of credit card bills and prompt dispute of any unauthorized charges are essential preventative measures.