Parked domains, often comprised of expired website addresses or common misspellings of popular sites, traditionally served as placeholders. Their primary purpose was to monetize the accidental traffic by displaying advertisements for third-party websites. In 2014, a study indicated that less than five percent of visitors to these parked domains were redirected to malicious sites, a figure that was considered relatively low even then. However, Infoblox’s recent extensive experiments paint a drastically different picture. Their findings indicate that over 90% of the time, visitors to a parked domain are now exposed to illegal content, deceptive scams, scareware pushing fraudulent antivirus subscriptions, or outright malware. This surge in malicious activity is attributed to a complex chain of advertising reselling, where traffic from parking companies is often bought and sold multiple times before reaching the end advertiser, who may have no direct relationship with the original parking service.
The Infoblox study details how parked domains leverage a sophisticated redirection system. When a user lands on a parked page, the system profiles their device and location using techniques like IP geolocation, device fingerprinting, and cookies. This profiling determines the most opportune malicious destination. David Brunsdon, a threat researcher at Infoblox, explained that visitors often pass through a series of redirects, sometimes involving one or two intermediary domains outside of the parking company itself, before reaching the final malicious payload. In some instances, if the system deems the visitor not worth targeting, they might be redirected to a decoy page mimicking legitimate e-commerce sites like Amazon.com or Alibaba.com, further obscuring the malicious intent.
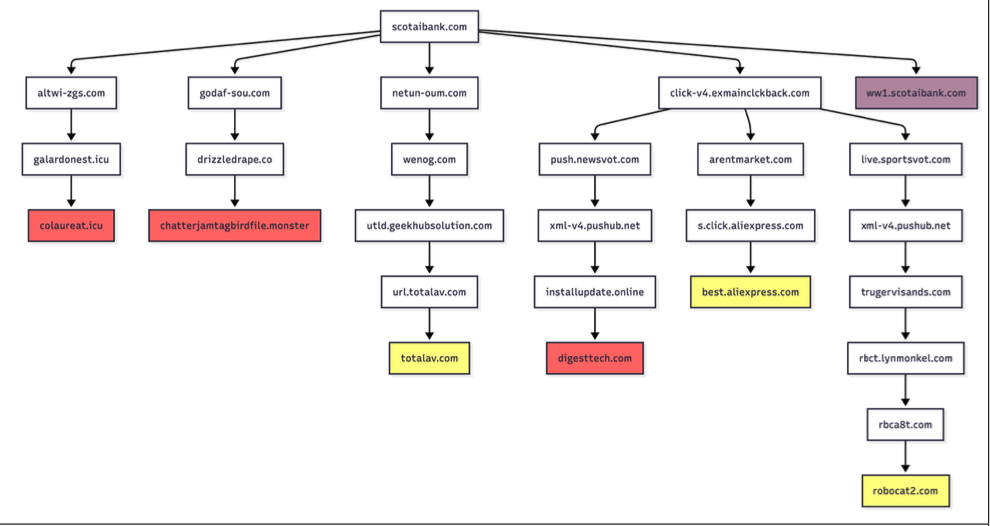
A particularly concerning aspect of the research is the exploitation of typosquatting domains, where malicious actors register domain names that are very similar to popular, legitimate websites. The study highlights the domain "scotaibank[.]com" as an example, which is a slight misspelling of "Scotiabank.com." While customers using a VPN might see a benign parking page, those accessing the site from a residential IP address are immediately redirected to deceptive content. The owner of "scotaibank[.]com" also controls a portfolio of nearly 3,000 similar domains, including "gmai[.]com." Alarmingly, "gmai[.]com" has been configured with its own mail server, meaning emails intended for legitimate Gmail users that are accidentally sent to this typosquatting domain are intercepted by scammers. This domain has been implicated in numerous business email compromise (BEC) campaigns, often using lures related to failed payments with trojan malware attachments.
The domain holder behind "scotaibank[.]com," identified through their use of the DNS server "torresdns[.]com," has established a wide net of typosquatting domains targeting a multitude of top internet destinations. This extensive list includes major platforms like Craigslist, YouTube, Google, Wikipedia, Netflix, TripAdvisor, Yahoo, eBay, and Microsoft. Infoblox has provided a defanged list of these domains, where the dots have been replaced with commas, to help users identify them.
Another threat actor identified by Infoblox operates the domain "domaincntrol[.]com," which differs from GoDaddy’s name servers by a single character. This actor has historically exploited DNS configuration errors to redirect users to malicious websites. Recent observations indicate a more targeted approach, with malicious redirects only occurring when queries for the misconfigured domain originate from visitors using Cloudflare’s DNS resolvers (1.1.1.1). All other visitors are presented with a page that fails to load, suggesting a sophisticated attempt to evade detection.
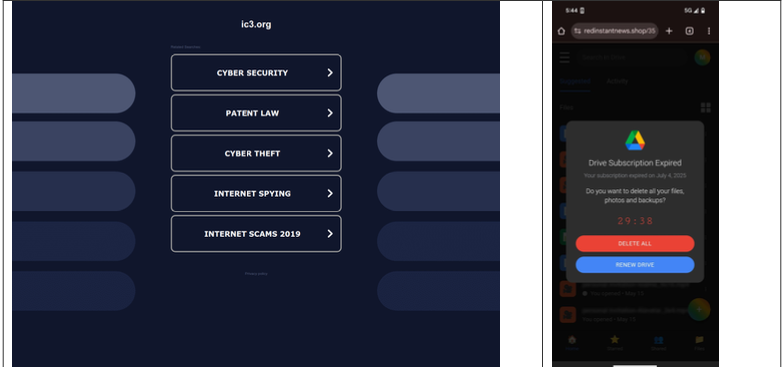
The researchers also found that even variations of legitimate government domains are being targeted. In one striking example, a researcher attempting to report a crime to the FBI’s Internet Crime Complaint Center (IC3) accidentally navigated to "ic3[.]org" instead of the correct "ic3[.]gov." Their mobile device was immediately redirected to a false "Drive Subscription Expired" page, a common scam. The report emphasizes that this could have easily led to the download of information-stealing malware or trojans.
Crucially, the Infoblox report clarifies that the malicious activity observed is not attributed to any single known entity, and the domain parking or advertising platforms themselves are not directly implicated in the malvertising. However, the study points to a systemic issue where the traffic, despite claims of working with reputable advertisers, is frequently sold through affiliate networks, leading to a lack of transparency and accountability. The end advertiser often has no direct relationship with the initial parking companies, making it difficult to trace the source of the malicious content.
Infoblox also suggests that recent policy changes by Google may have inadvertently exacerbated the risk posed by direct search abuse. Previously, Google AdSense defaulted to allowing ads on parked pages. However, in early 2025, Google implemented a setting where advertisers must actively opt-in to have their ads displayed on parked domains. While intended to improve ad quality, this shift might indirectly encourage malicious actors to leverage parked domains more aggressively, knowing that legitimate ad revenue streams are becoming more restrictive. The researchers conclude that the current environment makes direct navigation a perilous endeavor, urging users to exercise extreme caution and verify domain names before visiting them. The pervasive nature of these malicious redirects underscores the evolving tactics of cybercriminals and the critical need for enhanced user awareness and robust security measures. The study serves as a stark warning that the familiar act of typing a website address into a browser can now be a gateway to significant online harm.