A shadowy and prolific cybercriminal collective, known as ‘Scattered LAPSUS$ Hunters’ (SLSH), has been a persistent thorn in the side of major corporations throughout the year, consistently making headlines for its audacious data theft and widespread extortion campaigns. However, the tables appear to have turned for "Rey," the individual who served as the technical operator and public face of this notorious group. In a significant development, Rey confirmed his real-life identity and subsequently agreed to an interview after KrebsOnSecurity successfully tracked him down, initiating contact through his father.
The Scattered LAPSUS$ Hunters are understood to be a formidable amalgamation of three distinct hacking outfits: Scattered Spider, LAPSUS$, and ShinyHunters. The members of these gangs frequently congregate and communicate within shared chat channels on "the Com," a sprawling cybercriminal ecosystem primarily operating in English across a vast network of Telegram and Discord servers. This interconnectedness highlights the fluid and collaborative nature of modern cybercrime operations.
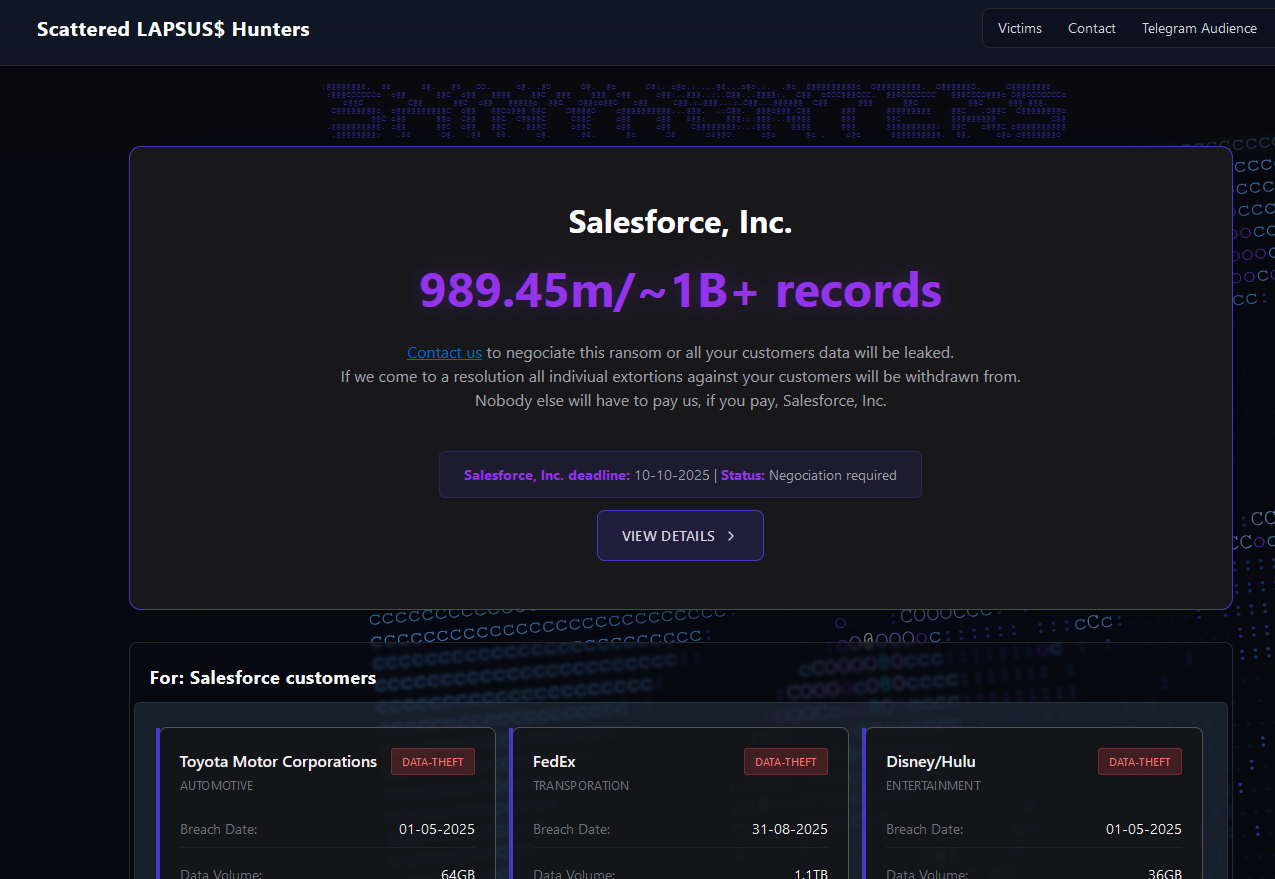
In May 2025, SLSH members orchestrated a sophisticated social engineering campaign that leveraged voice phishing techniques. Their objective was to trick unsuspecting targets into connecting a malicious application to their organization’s Salesforce portal. Following this initial breach, the group launched a dedicated data leak portal, threatening to publish the internal data of approximately three dozen companies from whom Salesforce data had allegedly been stolen. Among the prominent victims publicly named were global giants such as Toyota, FedEx, Disney/Hulu, and UPS, underscoring the far-reaching impact of their operations.
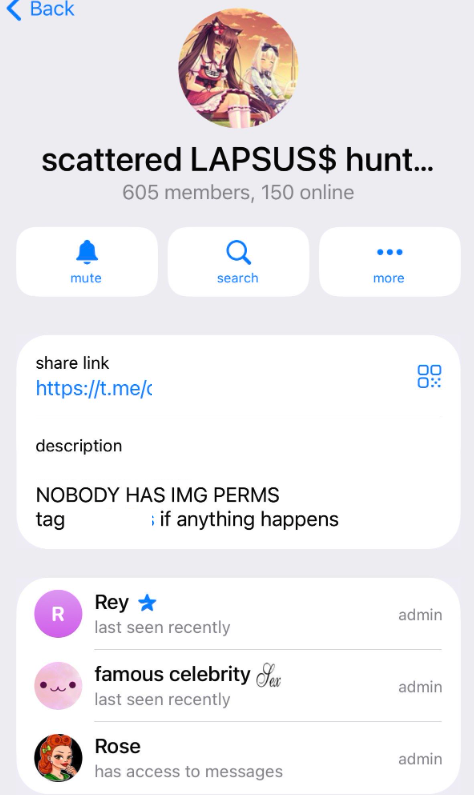
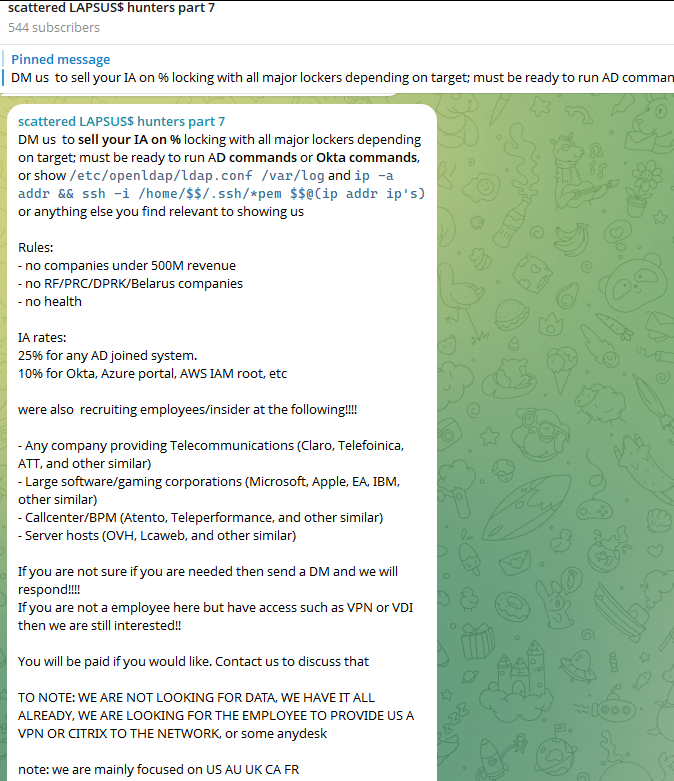
More recently, the SLSH Telegram channel featured an alarming proposition: an offer to recruit and reward "insiders" – employees within large corporations willing to share internal network access to their employers in exchange for a share of any ransom payments ultimately extorted from the victim companies. While SLSH had solicited insider access previously, their latest call for disgruntled employees gained significant traction on social media precisely as news broke that the prominent cybersecurity firm Crowdstrike had terminated an employee for allegedly sharing screenshots of internal systems with the hacker group. Crowdstrike, however, asserted that their systems were never compromised and that the matter had been handed over to law enforcement agencies.
Traditionally, SLSH members have relied on the encryptors of other ransomware gangs, utilizing malware from affiliate programs like ALPHV/BlackCat, Qilin, RansomHub, and DragonForce. However, in a significant strategic move last week, SLSH announced on its Telegram channel the launch of its own ransomware-as-a-service (RaaS) operation, branded as "ShinySp1d3r." The individual credited with releasing this new RaaS offering is a core SLSH member operating under the handle "Rey." At the time of this report, Rey was one of only three administrators of the SLSH Telegram channel. Prior to his involvement with SLSH, Rey held a position as an administrator for the data leak website of Hellcat, a ransomware group that emerged in late 2024 and was implicated in attacks against companies including Schneider Electric, Telefonica, and Orange Romania.
Further underscoring his deep involvement in the cybercriminal landscape, Rey also took over as administrator of the most recent iteration of BreachForums in 2024. BreachForums, an English-language cybercrime forum, has had its domain names seized multiple times by law enforcement, including the FBI and international authorities. In April 2025, Rey publicly posted on Twitter/X about yet another FBI seizure of BreachForums, indicating his awareness of and continued engagement with these platforms despite law enforcement actions.
On October 5, 2025, the FBI announced its latest seizure of the domains associated with BreachForums, characterizing it as a major criminal marketplace utilized by ShinyHunters and other threat actors for trafficking stolen data and facilitating extortion. The FBI stated that this takedown "removes access to a key hub used by these actors to monetize intrusions, recruit collaborators, and target victims across multiple sectors."
Incredibly, Rey made a series of critical operational security (OpSec) mistakes over the past year, which ultimately provided multiple avenues for investigators to ascertain and confirm his real-life identity and location. The unraveling of Rey’s digital facade is a complex narrative woven from various online activities and intelligence gathered by cybersecurity firms.
WHO IS REY?
According to insights from the cyber intelligence firm Intel 471, Rey was an active participant across various reincarnations of BreachForums for over two years, contributing more than 200 posts between February 2024 and July 2025. Intel 471 reports that Rey previously operated under the handle "Hikki-Chan" on BreachForums. His inaugural post on the platform detailed data allegedly stolen from the U.S. Centers for Disease Control and Prevention (CDC). In this February 2024 post concerning the CDC breach, Hikki-Chan provided a Telegram username, @wristmug, as a contact method.
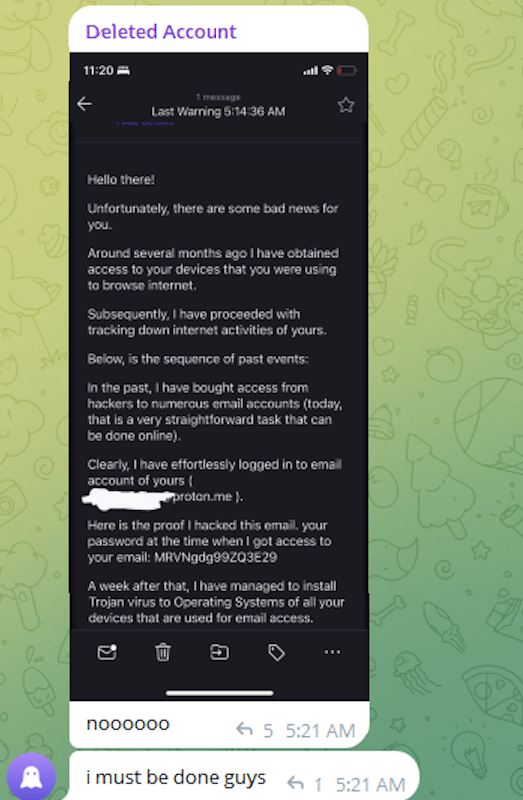
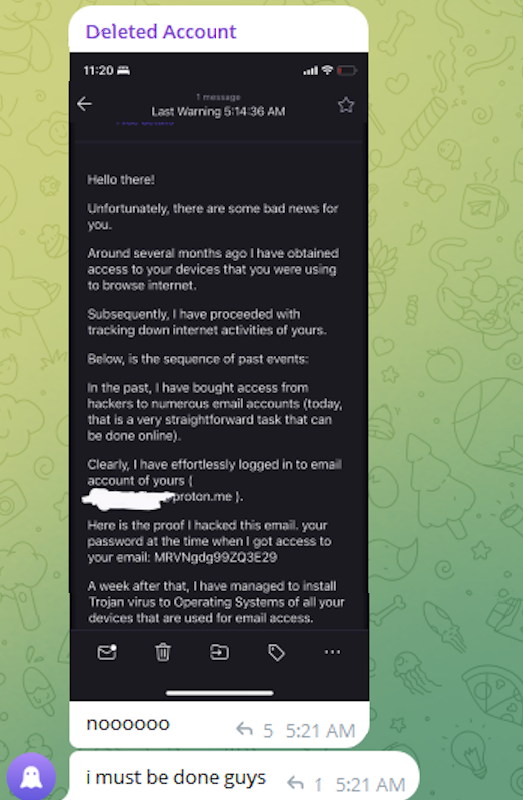
Later, in May 2024, the account @wristmug posted within a Telegram group chat named "Pantifan." The post contained a copy of an extortion email that the user claimed to have received, which included their email address and password. This message appeared to be part of an automated email scam, commonly known as "sextortion," which falsely claims the sender has compromised the recipient’s computer and recorded them watching pornography. These scams threaten to release fabricated video evidence to the recipient’s contacts unless a Bitcoin ransom is paid, and they typically reference a real password previously used by the victim to lend credibility. The @wristmug account, in mock horror, posted a screenshot of the scam message, exclaiming, "Noooooo, I must be done guys."
While @wristmug redacted the username portion of the email address in the screenshot, they failed to redact their previously used password. Crucially, they left the domain portion of their email address, "@proton.me," visible.
O5TDEV
A search for @wristmug’s distinctive 15-character password within the breach tracking service Spycloud revealed that it was associated with only one email address: [email protected]. Spycloud data indicates that these credentials were exposed at least twice in early 2024 due to the user’s device being infected with an infostealer trojan. This malware siphoned stored usernames, passwords, and authentication cookies. This finding was initially revealed in March 2025 by the cyber intelligence firm KELA.
Intel 471 further links the email address [email protected] to a BreachForums member who used the username "o5tdev." A Google search for this nickname brings up at least two website defacement archives, showcasing that a user named o5tdev was involved in defacing websites with pro-Palestinian messages. One screenshot illustrates that o5tdev was part of a collective known as the "Cyb3r Drag0nz Team."
A 2023 report from SentinelOne described the Cyb3r Drag0nz Team as a hacktivist group with a history of launching Distributed Denial of Service (DDoS) attacks, conducting cyber defacements, and engaging in data leak activities. SentinelOne reported, "Cyb3r Drag0nz Team claims to have leaked data on over a million of Israeli citizens spread across multiple leaks. To date, the group has released multiple .RAR archives of purported personal information on citizens across Israel."
The cyber intelligence firm Flashpoint notes that the Telegram user @05tdev was active in 2023 and early 2024, posting in Arabic on anti-Israel channels such as "Ghost of Palestine."
"I’M A GINTY"
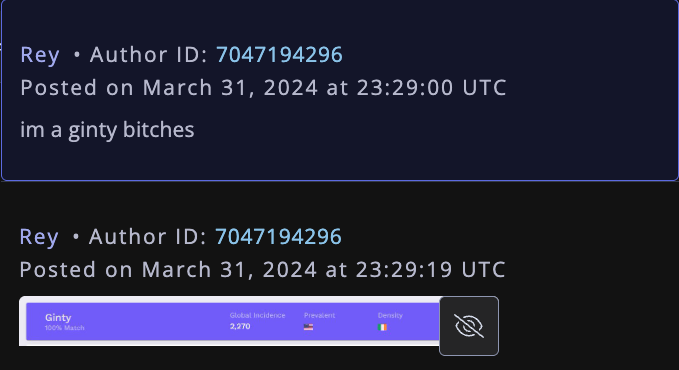
Flashpoint’s analysis shows that Rey’s Telegram account (ID7047194296) was particularly active in a cybercrime-focused channel called "Jacuzzi." Within this channel, the user shared several personal details, including that their father was an airline pilot. In 2024, Rey claimed to be 15 years old and asserted family connections to Ireland. Specifically, Rey mentioned in several Telegram chats that he had Irish heritage and even posted a graphic illustrating the prevalence of the surname "Ginty."

Spycloud indexed hundreds of credentials stolen from [email protected]. This data suggests that Rey’s computer is a shared Microsoft Windows device located in Amman, Jordan. The credential data stolen from Rey in early 2024 indicates that multiple users shared the infected PC, and that all shared the same last name, Khader, and an address in Amman, Jordan. The "autofill" data extracted from Rey’s family PC contains an entry for a 46-year-old individual named Zaid Khader, noting that his mother’s maiden name was Ginty. The infostealer data also reveals that Zaid Khader frequently accessed internal websites for employees of Royal Jordanian Airlines.
MEET SAIF
The infostealer data unequivocally identifies Rey’s full name as Saif Al-Din Khader. After initial attempts to contact Saif directly proved unsuccessful, KrebsOnSecurity sent an email to his father, Zaid. The message invited Zaid to respond via email, phone, or Signal, explaining that his son appeared to be deeply entangled in a serious cybercrime conspiracy.
Less than two hours later, a Signal message was received from Saif, who stated that his father suspected the email was a scam and had forwarded it to him. "I saw your email, unfortunately I don’t think my dad would respond to this because they think its some ‘scam email,’" Saif wrote, adding, "So I decided to talk to you directly." Saif, who mentioned he would be turning 16 the following month, explained that he had already been contacted by European law enforcement officials and was attempting to extricate himself from SLSH.
When questioned about his involvement in releasing SLSH’s new ShinySp1d3r RaaS offering, Saif explained that he couldn’t simply quit the group abruptly. "Well I cant just dip like that, I’m trying to clean up everything I’m associated with and move on," he stated. He also shared that ShinySp1d3r is essentially a reworked version of the Hellcat ransomware, enhanced with AI tools, and admitted, "I gave the source code of Hellcat ransomware out basically."
Saif claims he recently reached out independently to the Telegram account for "Operation Endgame," a law enforcement operation targeting cybercrime services, vendors, and their customers. "I’m already cooperating with law enforcement," Saif asserted. "In fact, I have been talking to them since at least June. I have told them nearly everything. I haven’t really done anything like breaching into a corp or extortion related since September."
Saif suggested that a published story about him at this juncture could jeopardize any further cooperation he might be able to provide. He also expressed uncertainty about whether U.S. or European authorities had contacted the Jordanian government regarding his involvement with the hacking group. "A story would bring so much unwanted heat and would make things very difficult if I’m going to cooperate," Saif explained. "I’m unsure whats going to happen they said they’re in contact with multiple countries regarding my request but its been like an entire week and I got no updates from them."
Saif shared a screenshot indicating he had contacted Europol authorities late the previous month. However, he could not name any specific law enforcement officials who were responding to his inquiries, and KrebsOnSecurity was unable to independently verify his claims. "I don’t really care I just want to move on from all this stuff even if its going to be prison time or whatever they gonna say," Saif concluded.