A rapidly expanding Internet-of-Things (IoT) botnet, dubbed "Kimwolf," has infected over two million devices and is actively being utilized to launch massive distributed denial-of-service (DDoS) attacks and relay a wide array of malicious internet traffic, including ad fraud, account takeover attempts, and content scraping. The botnet’s insidious ability to scan and infect other IoT devices within the local networks of its compromised hosts poses a significant and concerning threat to organizations, with recent research revealing a surprising prevalence within government and corporate networks.
Kimwolf’s exponential growth in late 2025 was largely facilitated by its exploitation of "residential proxy" services. These services, often marketed as a means to anonymize and localize web traffic, allow users to route their internet activity through devices in diverse geographic locations globally. The malware responsible for turning these devices into proxy nodes is frequently bundled discreetly with mobile applications and games, surreptitiously co-opting the infected device to relay malicious and abusive internet traffic.
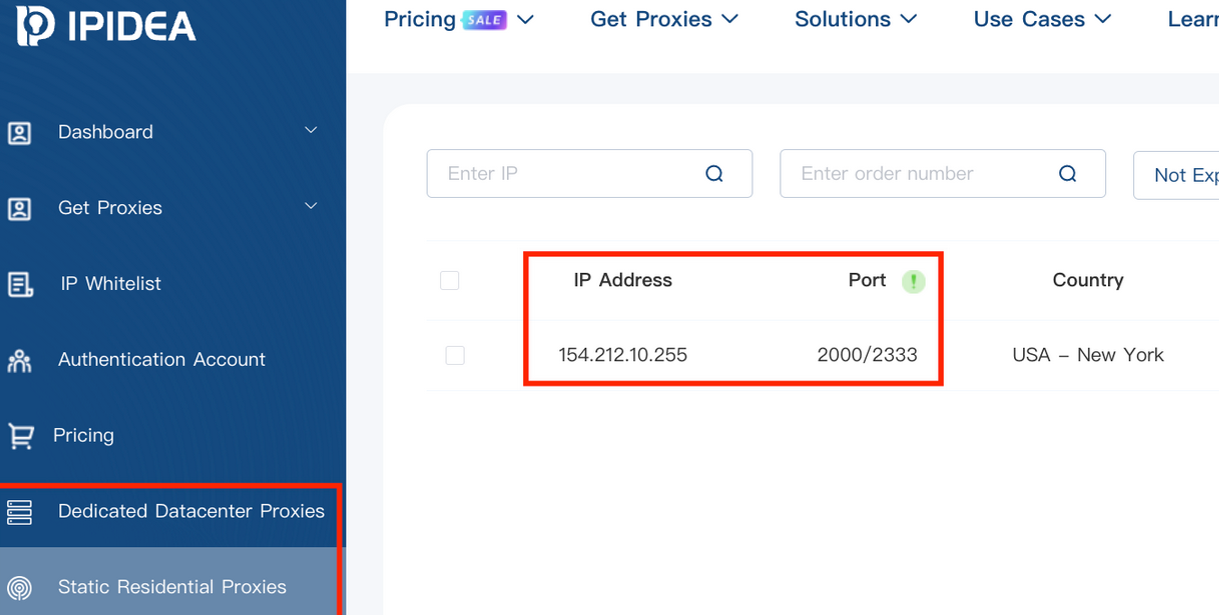
A primary target of Kimwolf has been IPIDEA, a Chinese residential proxy service boasting millions of proxy endpoints. The operators of Kimwolf discovered a critical vulnerability: they could forward malicious commands to the internal networks of IPIDEA’s proxy endpoints. This allowed them to programmatically scan for and infect other vulnerable devices connected to the same local network. The vast majority of devices compromised through this lateral movement technique have been unofficial Android TV streaming boxes. These devices, often running on the Android Open Source Project rather than certified Android TV OS and lacking Google Play Protect certification, are typically marketed as a one-time purchase solution for accessing pirated video content. Alarmingly, many of these TV boxes come with residential proxy software pre-installed and lack basic security or authentication, making them easy targets for malware if directly accessible.
While IPIDEA and other affected proxy providers have reportedly implemented measures to block Kimwolf’s upstream propagation with varying degrees of success, the malware continues to reside on millions of infected devices.
Despite the initial association with compromised Android TV boxes and residential proxy networks, which might suggest limited impact on corporate environments, new research from the security firm Infoblox paints a starkly different picture. A recent review of Infoblox’s customer traffic revealed that nearly 25 percent of their clients made queries to Kimwolf-related domain names since the botnet first emerged around October 1, 2025. These affected customers span the globe and encompass a wide range of industry verticals, including education, healthcare, government, and finance. Infoblox clarified that this statistic indicates that at least one device within these customer networks was acting as an endpoint for a residential proxy service targeted by Kimwolf. While a query signifies a scan, not necessarily a successful compromise, it highlights the botnet’s reach and its attempt to probe internal networks. Lateral movement would only succeed if vulnerable devices were found and DNS resolution was not blocked.
Synthient, a startup specializing in tracking proxy services and the first to disclose Kimwolf’s unique propagation methods, observed an alarming number of IPIDEA proxy endpoints within government and academic institutions worldwide. Synthient identified at least 33,000 affected internet addresses at universities and colleges, and nearly 8,000 IPIDEA proxies operating within various U.S. and international government networks.
Further insights from the proxy tracking service Spur, presented in a webinar on January 16, revealed residential proxies from IPIDEA and ten other potentially vulnerable proxy services operating within nearly 300 government-owned and operated networks. Additionally, Spur found proxies within 318 utility companies, 166 healthcare organizations or hospitals, and 141 companies in the banking and finance sectors.
Riley Kilmer, Co-Founder of Spur, expressed significant concern over the presence of IPIDEA proxies within U.S. Department of Defense (DoD) networks, stating, "I looked at the 298 [government] owned and operated [networks], and so many of them were DoD… which is kind of terrifying that DoD has IPIDEA and these other proxy services located inside of it." Kilmer acknowledged that network segmentation might mitigate immediate risks, but emphasized the inherent danger: "If a device goes in, anything that device has access to the proxy would have access to."
Kilmer highlighted Kimwolf as a prime example of how a single residential proxy infection can rapidly escalate into significant organizational security problems. He explained that proxy services offer attackers a seemingly simple method to probe other devices within an organization’s local network. "If you know you have [proxy] infections that are located in a company, you can chose that [network] to come out of and then locally pivot," Kilmer noted. "If you have an idea of where to start or look, now you have a foothold in a company or an enterprise based on just that."
This report is the third in a series examining the Kimwolf botnet. Future installments will delve into the individuals and companies in China linked to the Badbox 2.0 botnet, an umbrella term for a vast number of Android TV streaming box models that are shipped with pre-installed residential proxy malware and a complete lack of security or authentication.
Further reading on the Kimwolf botnet and related threats is available through the following resources:
- The Kimwolf Botnet is Stalking Your Local Network
- Who Benefitted from the Aisuru and Kimwolf Botnets?
- A Broken System Fueling Botnets (Synthient)