The year 2025 marked a notable shift in the fight against crypto-related cybercrime, as reported by Web3 security platform Scam Sniffer. Their comprehensive analysis, focusing on signature-based phishing across various Ethereum Virtual Machine (EVM) chains, unveiled a dramatic 83% year-over-year reduction in total losses. The collective sum siphoned off by crypto phishing attacks plummeted to an estimated $83.85 million, a stark contrast to the staggering nearly $494 million lost in 2024. This impressive decline signals a potential turning point, possibly attributed to enhanced security measures, increased user awareness, or more effective detection and prevention tools deployed across the ecosystem.
Beyond the financial figures, the human toll also saw a significant decrease. The number of victims affected by these malicious campaigns fell by 68%, settling at 106 individuals in 2025 compared to the previous year. This reduction in both monetary losses and victim count provides a glimmer of hope for the burgeoning Web3 space, suggesting that collective efforts to bolster security and educate users may be bearing fruit. EVM chains, which are blockchain networks compatible with the Ethereum Virtual Machine, represent a vast and interconnected ecosystem where a majority of decentralized applications (dApps) and digital assets reside. The focus on these chains by Scam Sniffer underscores their critical importance in the broader crypto landscape.
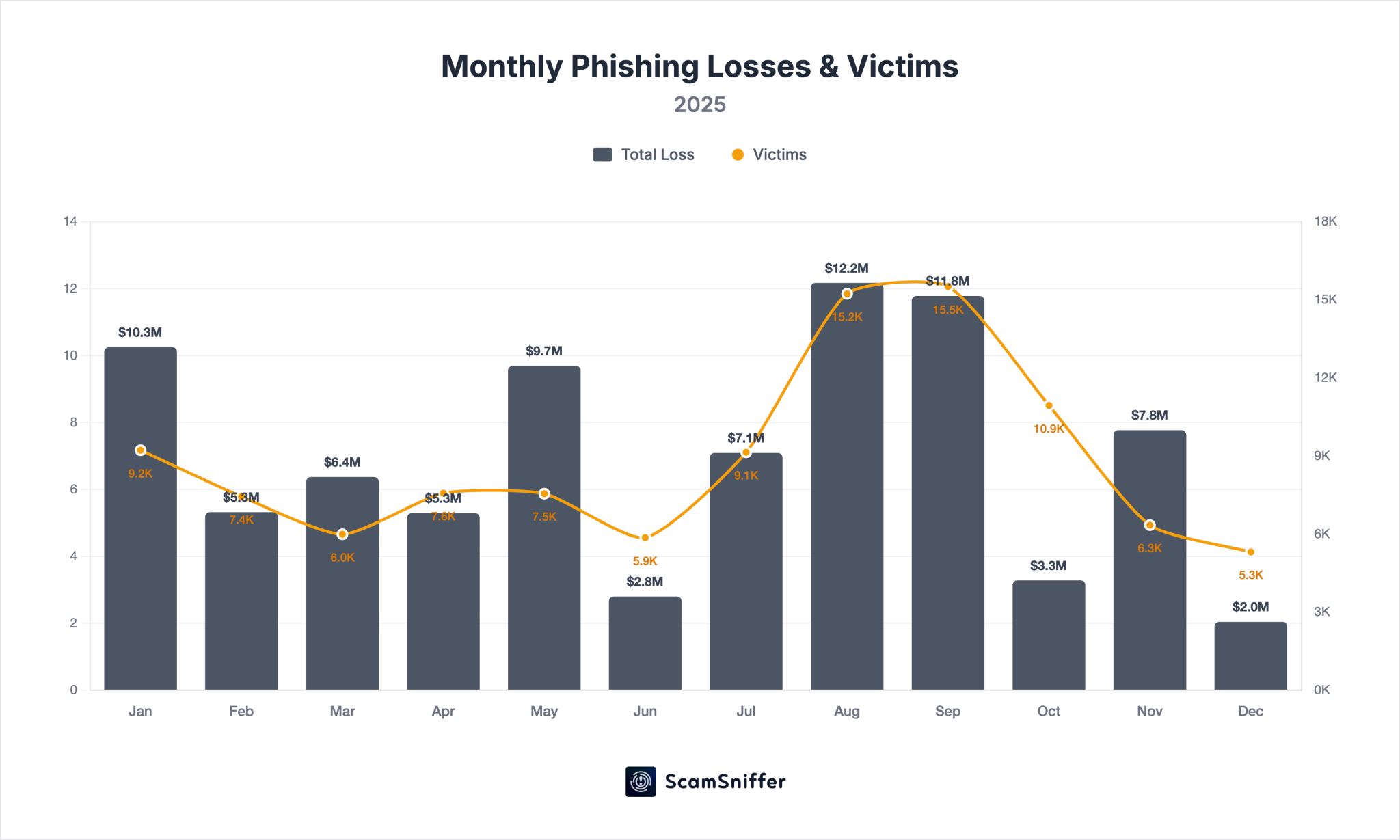
However, the report was quick to temper optimism with a crucial caveat: phishing activity has not vanished. Instead, it has proven to be remarkably adaptable, closely mirroring the ebb and flow of market cycles. This observation points to a strategic evolution among attackers, who appear to meticulously time their operations to coincide with periods of heightened on-chain activity. The third quarter of 2025 serves as a prime example, registering the highest phishing losses at $31 million, which accounted for nearly 29% of the year’s total. This period notably coincided with Ethereum’s (ETH) strongest rally of the year, underscoring the direct correlation between market vibrancy and scam prevalence.
"When markets are active, overall user activity increases, and a percentage fall victim — phishing operates as a probability function of user activity," the report articulated. This concept suggests that the sheer volume of transactions, new user registrations, and general engagement during bull markets creates a larger attack surface and more opportunities for scammers to ensnare unsuspecting individuals. During these frenzied periods, users might be more susceptible to emotional decision-making, rushing into transactions, or overlooking red flags in their eagerness to participate in market movements. Monthly losses vividly illustrated this pattern, ranging from a relatively quiet $2.04 million in December, typically a slower month for crypto markets, to a peak of $12.17 million in August, a period of heightened market euphoria and transaction volume. This cyclical nature of phishing losses highlights the continuous need for vigilance, irrespective of market conditions.
The landscape of attack vectors also saw significant shifts and the emergence of new threats in 2025. The largest single phishing theft of the year, a staggering $6.5 million, occurred in September and involved a malicious Permit signature. This incident underscored the persistent efficacy of Permit and Permit2 approvals as potent tools for attackers. For context, Permit and Permit2 are token standards that allow users to approve token transfers without directly sending a transaction, instead signing an off-chain message. While designed for convenience and gas efficiency, malicious actors exploit these mechanisms by tricking users into signing approvals that grant control over their tokens to the scammer’s wallet drainer. Overall, Permit-based attacks were alarmingly prevalent, accounting for 38% of all incidents exceeding $1 million in losses, cementing their status as a preferred method for high-value targets.

However, 2025 also marked the chilling arrival of a novel attack vector, showcasing the relentless innovation of cybercriminals. Shortly after Ethereum’s Pectra upgrade, EIP-7702-based malicious signatures began appearing. The Pectra upgrade, a significant protocol-level change, introduced features related to account abstraction, a concept aimed at making crypto wallets more flexible and user-friendly by allowing them to behave more like smart contracts. EIP-7702 specifically allows for temporary, code-backed accounts to be used for transactions. Attackers swiftly adapted, exploiting this new capability to bundle multiple harmful actions into a single user signature. This sophisticated method effectively bypasses traditional security checks, making it harder for users to discern the true intent of a transaction. Two major EIP-7702 cases in August alone resulted in $2.54 million in losses, serving as a stark reminder of how rapidly malicious actors can integrate and weaponize protocol-level changes, turning innovative features into new avenues for exploitation.
A deeper dive into the report’s findings reveals a strategic pivot by attackers. While the overall losses decreased, the nature of the attacks shifted. Large-scale incidents declined considerably, with only 11 cases exceeding $1 million in 2025, a significant drop from 30 such incidents in 2024. This trend suggests that high-profile, "whale" targeting might be becoming more challenging for scammers. In response, attackers are increasingly favoring lower-value, higher-volume strategies. The average loss per victim fell dramatically to $790, indicating a clear shift toward broader, retail-focused campaigns rather than isolated, audacious thefts. This means that while individual losses might be smaller, the cumulative impact across a larger user base remains substantial, and the threat is now more pervasive for the average crypto holder. This strategy of "death by a thousand cuts" makes detection and prevention more complex, as smaller amounts might not trigger the same alarms as multi-million dollar exploits. "The drainer ecosystem remains active — as old drainers exit, new ones emerge to fill the gap," the report concluded, emphasizing the persistent and dynamic nature of these criminal networks.
Connecting these insights to the broader cybersecurity landscape, it’s evident that phishing is but one facet of the multifaceted threats facing the crypto space. As Cointelegraph previously reported, crypto-related losses from hacks and cybersecurity exploits in general also experienced a downturn towards the end of 2025. Specifically, December saw losses drop to approximately $76 million, a 60% decrease from November’s $194.2 million, according to data from PeckShield. While PeckShield’s data encompasses a wider array of hacks beyond just signature-based phishing, the general trend of declining losses in the final month of the year aligns with a broader cooling in the market and potentially, a more robust security posture across the industry.
Despite the overall reduction, significant incidents continued to occur. PeckShield recorded 26 major incidents in December, highlighting that even with reduced losses, attack activity remained persistent. The largest case involved a staggering $50 million address poisoning scam, a cunning technique where attackers send small, zero-value transactions to a victim’s wallet from an address that closely resembles a legitimate, frequently used address. The goal is to trick the victim into accidentally copying the malicious lookalike address from their transaction history when initiating a real transfer, thereby misdirecting funds. Another incident saw $27.3 million lost through a private key leak tied to a multi-signature wallet. Multi-signature wallets, designed for enhanced security by requiring multiple approvals for transactions, are typically considered safer. However, a private key leak, whether through social engineering, malware, or insider threat, can compromise even these advanced security mechanisms. These incidents underscore that while phishing might be declining, other vectors of attack, often more sophisticated or reliant on human error, continue to pose significant risks.
The findings from Scam Sniffer and PeckShield collectively paint a nuanced picture of the crypto security landscape in 2025. On one hand, the substantial reduction in phishing losses is a commendable achievement, reflecting progress in user education, security tool development, and industry-wide collaboration. The 83% drop is a testament to the continuous efforts by security platforms, developers, and vigilant users to combat these pervasive threats. However, the reports also serve as a critical reminder that the battle is far from over. Attackers are not simply disappearing; they are adapting, evolving their tactics, and shifting their focus. The emergence of new attack vectors like EIP-7702 exploits, the pivot towards retail-focused, high-volume, lower-value campaigns, and the persistent threat of other exploit types like address poisoning and private key leaks mean that vigilance, continuous education, and robust security practices remain paramount. As the crypto ecosystem continues to grow and innovate, so too will the methods of those seeking to exploit it, making the ongoing cat-and-mouse game between security and vulnerability a permanent feature of the Web3 frontier. Users are strongly advised to regularly revoke token approvals, utilize hardware wallets for significant holdings, exercise extreme caution with unfamiliar links or messages, and stay informed about the latest scam techniques to protect their digital assets.