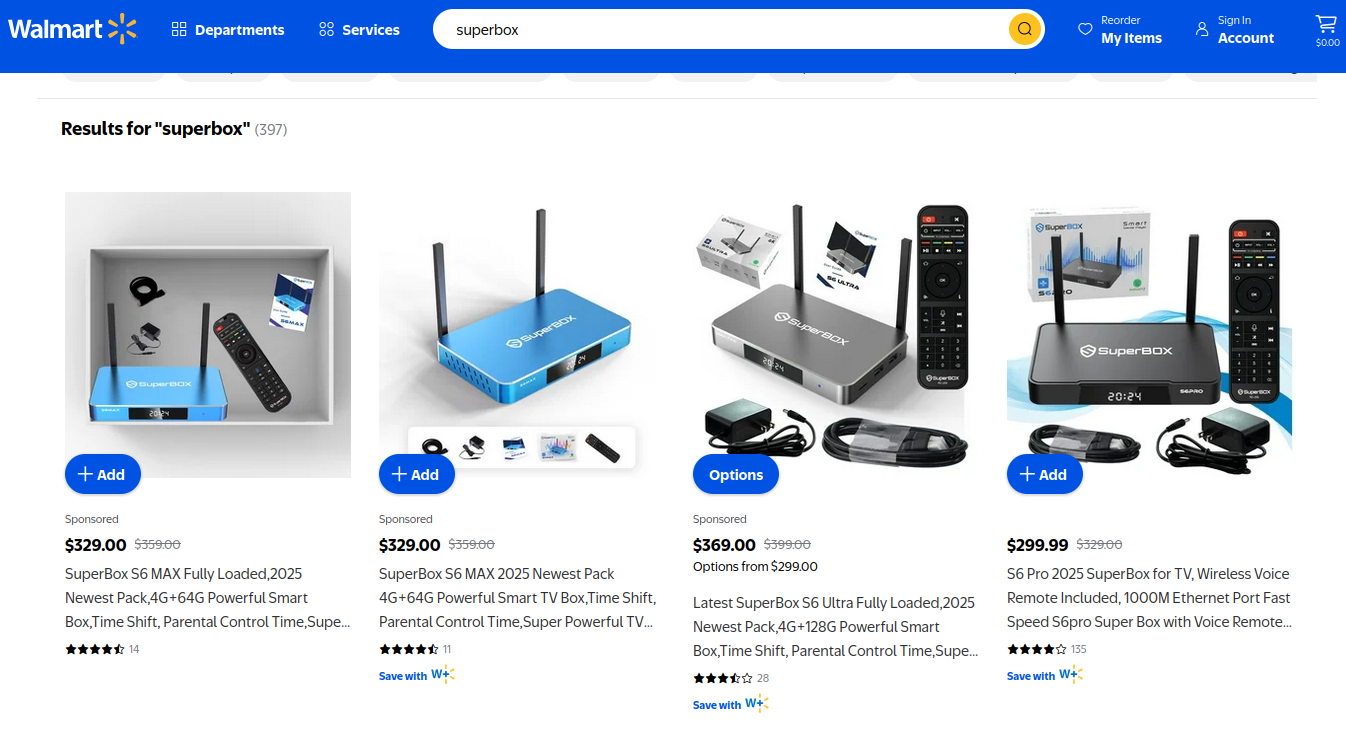
On the surface, the Superbox media streaming devices, readily available at major retailers like BestBuy and Walmart, present an enticing proposition: unlimited access to over 2,200 pay-per-view and popular streaming services such as Netflix, ESPN, and Hulu, all for a one-time cost of approximately $400. However, a stark warning from security experts reveals a more sinister reality. These seemingly affordable TV boxes are embedded with intrusive software that hijacks the user’s network, forcing it to relay Internet traffic for others. This rerouted traffic is frequently linked to illicit cybercrime activities, including widespread advertising fraud and sophisticated account takeovers.
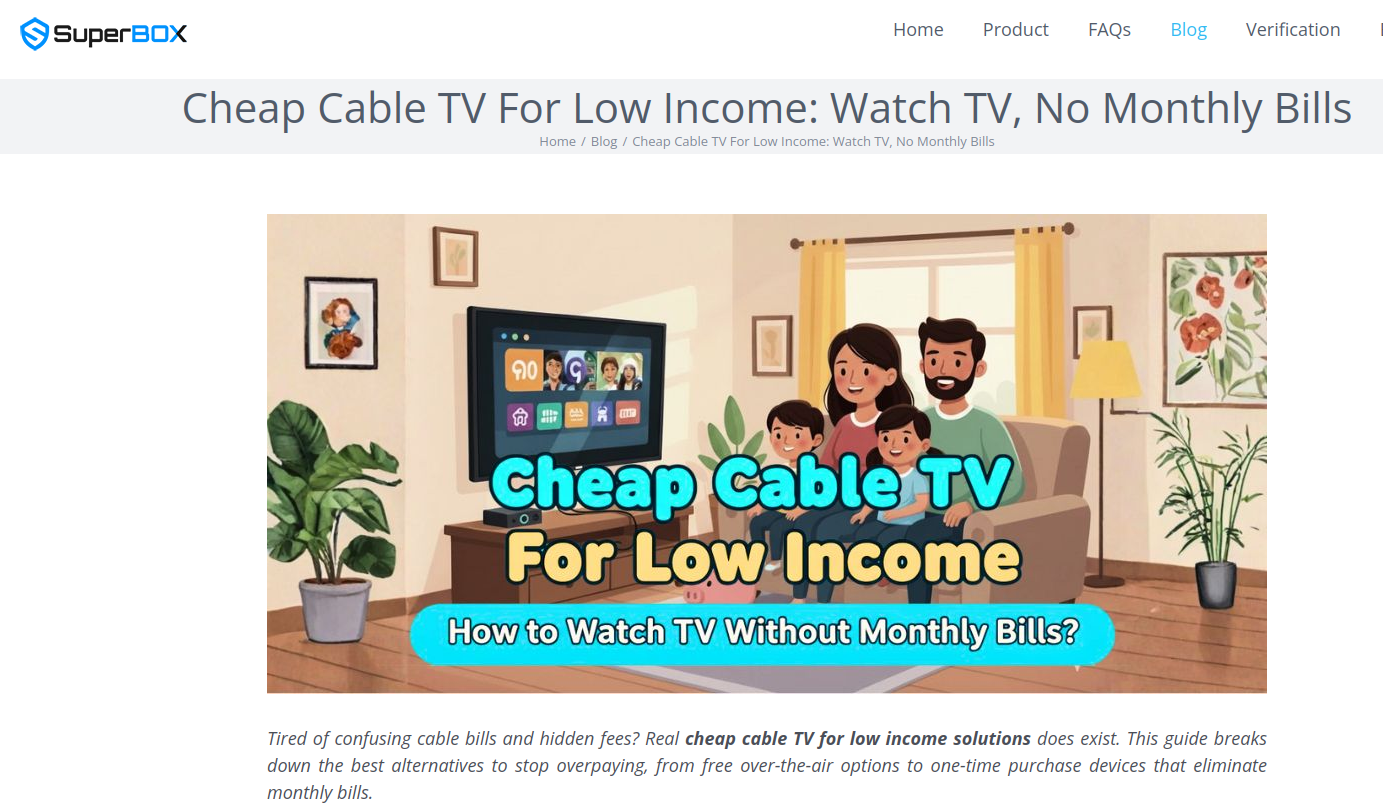
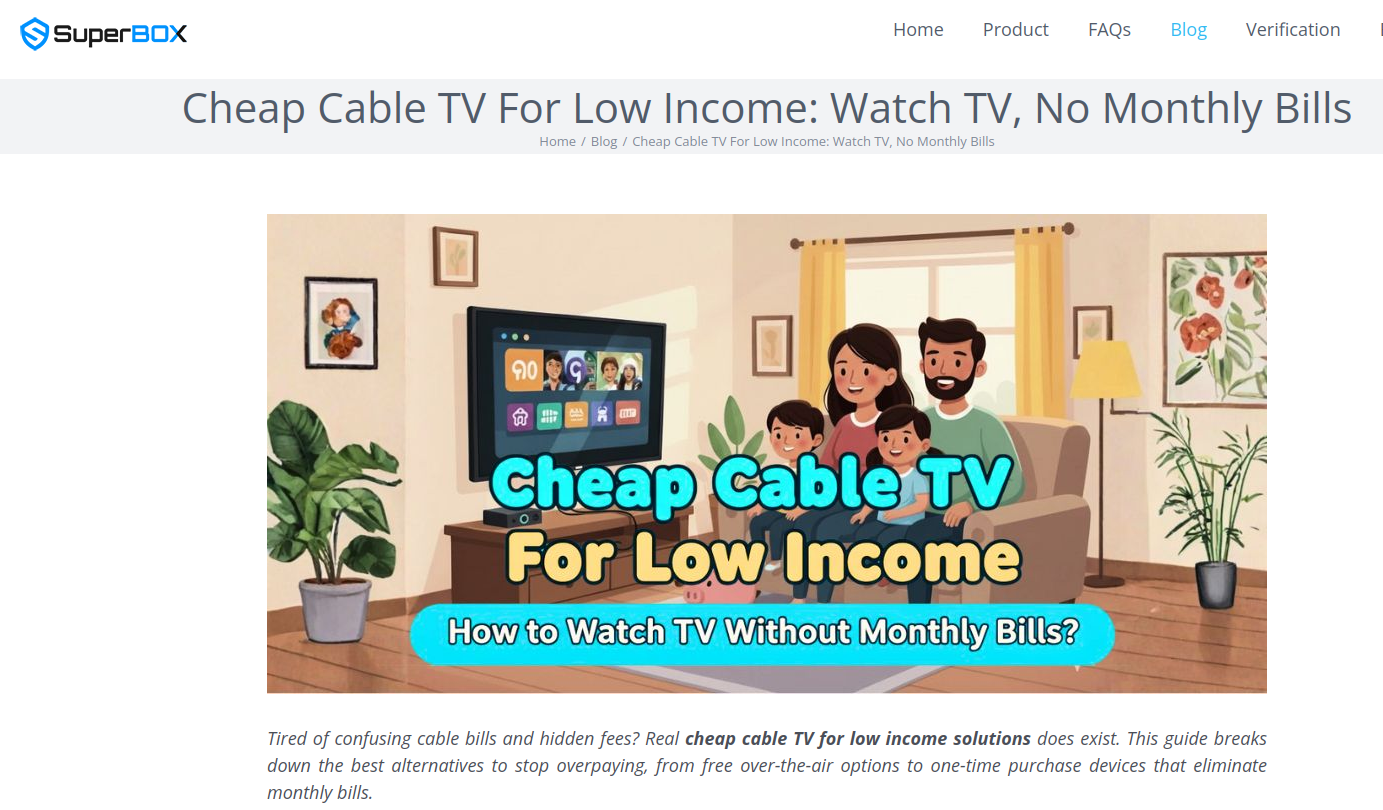
The Superbox markets itself as the ultimate solution for households seeking to stream an exhaustive library of television and movie content without the perpetual burden of monthly subscription fees. Its advertising aggressively targets consumers tired of convoluted cable bills and hidden charges, promoting itself as a "Cheap Cable TV for Low Income" solution, offering a way to "Watch TV, No Monthly Bills." The company’s website boldly claims that its streaming capabilities do not violate U.S. copyright law, stating, "SuperBox is just like any other Android TV box on the market, we can not control what software customers will use… And you won’t encounter a law issue unless uploading, downloading, or broadcasting content to a large group."
While the sale and basic use of the Superbox itself are not inherently illegal – it can function legitimately as a conduit for content from services where users already hold paid subscriptions – this is not the primary draw for consumers willing to spend $400. The allure lies in the promise of accessing those 2,200+ channels without any recurring payments, which necessitates the installation of specific apps designed for this purpose. Superbox’s homepage conspicuously states that it "does not sell access to or preinstall any apps that bypass paywalls or provide access to unauthorized content," asserting that they merely provide the hardware, and customers are solely responsible for their app choices and adherence to copyright laws.
However, this claim is technically misleading. To unlock the vast array of channels, users must first configure the device to update itself, a process that involves replacing Google’s official Play Store with an unofficial alternative, such as the "App Store" or "Blue TV Store." This circumvention is necessary because the Superbox does not run a Google-certified Android TV system, rendering official apps incompatible. Only after this unofficial app store is installed do the specialized streaming apps for the Superbox become available for download, operating entirely outside of Google’s regulated ecosystem.
Security experts explain that while these Android streaming boxes deliver on their promise of enabling access to normally paid-for content, the apps that facilitate this access also ensnare the user’s Internet connection into a distributed residential proxy network. This network leverages the devices to relay traffic for unknown third parties. Ashley, a senior solutions engineer at cyber intelligence firm Censys, who requested her first name be used, highlighted the concerning findings from Censys’s analysis of Superbox models, including one purchased directly from BestBuy. "I’m sure a lot of people are thinking, ‘Hey, how bad could it be if it’s for sale at the big box stores?’ But the more I looked, things got weirder and weirder," Ashley stated.
Her investigation revealed that Superbox devices immediately establish contact with a server belonging to Tencent QQ, a Chinese instant messaging service, and a residential proxy service known as Grass IO. Grass, operating under getgrass[.]io, describes itself as a "decentralized network that allows users to earn rewards by sharing their unused Internet bandwidth with AI labs and other companies." Their website explains that buyers seek unused bandwidth to access a diverse range of IP addresses for market research or web scraping to train AI.
Andrej Radonjic, founder of Grass, expressed unfamiliarity with Superbox and denied any affiliation, suggesting that the boxes are distributing an "unethical proxy network" that users are attempting to exploit. He emphasized that Grass is an opt-in network where users download the app to monetize their bandwidth, and that the company actively works to identify and block network abusers who attempt to misuse their service.
Superbox’s parent company, Super Media Technology Company Ltd., lists a UPS store in Fountain Valley, Calif., as its address and has not responded to inquiries. Investigations into Grass’s compensation plan reveal a structure heavily reliant on "grass points," earned through app usage and recruited affiliates, with significant recruitment requirements to redeem points, suggesting a potential multi-level marketing (MLM) scheme. Radonjic confirmed that Grass has undergone corporate restructuring but maintains these are administrative changes without operational impact.
Further technical analysis by Censys’s Ashley uncovered more alarming details about the Superbox devices. The initial connection to Tencent QQ was a significant red flag, but the presence of powerful network analysis and remote access tools like Tcpdump and Netcat on a supposed streaming device was particularly concerning. Ashley reported, "This thing DNS hijacked my router, did ARP poisoning to the point where things fall off the network so they can assume that IP, and attempted to bypass controls. I have root on all of them now, and they actually have a folder called ‘secondstage.’ These devices also have Netcat and Tcpdump on them, and yet they are supposed to be streaming devices."

Superbox models, along with numerous similar Android streaming devices, are widely available across major e-commerce platforms like Amazon, BestBuy, Newegg, and Walmart, often sold by third-party merchants but fulfilled by the platforms themselves. While Amazon has reportedly taken action against Superbox listings, similar devices persist under more generic descriptions. Superbox reportedly relies on influencers on platforms like YouTube and TikTok for promotion, offering them a substantial 50 percent commission, a unusually high rate that Ashley suggests indicates a focus on network building rather than pure profit.
The Superbox is just one example within a vast market of unbranded Android TV boxes. These devices, while offering "free" streaming content, are frequently pre-loaded with malware or require the installation of third-party apps that engage the user’s internet connection in fraudulent activities. In July 2025, Google filed a lawsuit against 25 unidentified defendants, labeling them the "BadBox 2.0 Enterprise," a botnet comprising over ten million Android streaming devices involved in advertising fraud. This botnet compromised devices before purchase and could also infect them through malicious apps downloaded from unofficial marketplaces. Several devices implicated in Google’s lawsuit, such as the X88Pro 10 and T95, remain available on Amazon.
This lawsuit followed a June 2025 advisory from the FBI, which warned that cybercriminals were gaining unauthorized access to home networks by pre-installing malicious software or infecting devices during setup through backdoor-laden applications. These compromised IoT devices, once connected, become part of botnets like BADBOX 2.0 and residential proxy services used for malicious activities. The FBI noted that BADBOX 2.0 emerged after the disruption of the original BADBOX campaign in 2024, which itself was identified in 2023 and primarily involved Android devices compromised with backdoor malware before sale.
Riley Kilmer, founder of Spur, a company that tracks residential proxy networks, stated that Badbox 2.0 served as a distribution platform for IPidea, a Chinese entity now recognized as the world’s largest residential proxy network. IPidea is widely believed to be a rebrand of the 911S5 Proxy, a service previously sanctioned by the U.S. Department of the Treasury for operating a botnet that facilitated billions of dollars in fraud. According to proxy detection service Synthient, a significant portion of IPidea’s traffic is linked to ad fraud and credential stuffing. Kilmer acknowledges that companies like Grass might be truthful about their legitimate customers using their services for AI training through web scraping, but notes that these proxy networks are increasingly used to obscure aggressive data collection. "Web crawling and scraping has always been a thing, but AI made it like a commodity, data that had to be collected," Kilmer explained.
The appeal of devices like Superbox is growing as popular network television and sporting events migrate to subscription streaming services, leading consumers to realize they are spending as much, if not more, on streaming subscriptions as they did on traditional cable. These no-name streaming devices exemplify the adage, "If something is free, you are the product." While Superbox owners may point to their $400 purchase as proof of payment, this initial cost does not absolve them of the ongoing implications, nor does it guarantee they are the only ones adversely affected.
Many Superbox users might not be concerned about their internet connection being used to facilitate ad fraud or account takeovers, viewing it as a worthwhile trade-off for avoiding multiple monthly streaming bills. However, a significant number of individuals who purchase or receive these devices likely have little understanding of the underlying bargain they are making when connecting them to their home network.
Superbox employs elaborate linguistic strategies to assert that its products do not violate copyright laws, placing the onus on customers to ensure compliance with local regulations. However, consumers in the United States should be aware that using these devices for unauthorized streaming contravenes the Digital Millennium Copyright Act (DMCA), potentially leading to legal action, fines, and service interruptions from their Internet Service Provider.
The FBI has outlined several tell-tale signs that a streaming device may be malicious:
- The presence of suspicious app marketplaces.
- Requirements to disable Google Play Protect.
- Generic TV streaming devices advertised as "unlocked" or capable of accessing free content.
- IoT devices from unrecognizable brands.
- Android devices not certified by Play Protect.
- Unexplained or suspicious internet traffic.
The Electronic Frontier Foundation offers further details on these indicators in their explainer.