China-based phishing groups, notorious for their relentless barrage of scam SMS messages concerning supposed package issues or unpaid toll fees, have unveiled a new lucrative venture just as the holiday shopping season kicks into high gear: sophisticated phishing kits designed to mass-produce convincing, yet entirely fake, e-commerce websites. These platforms are engineered to efficiently harvest customer payment card data, which is then converted into mobile wallets for Apple and Google. Security experts reveal that these same prolific phishing syndicates are now leveraging SMS lures that promise unclaimed tax refunds and valuable mobile rewards points to ensnare unsuspecting consumers.
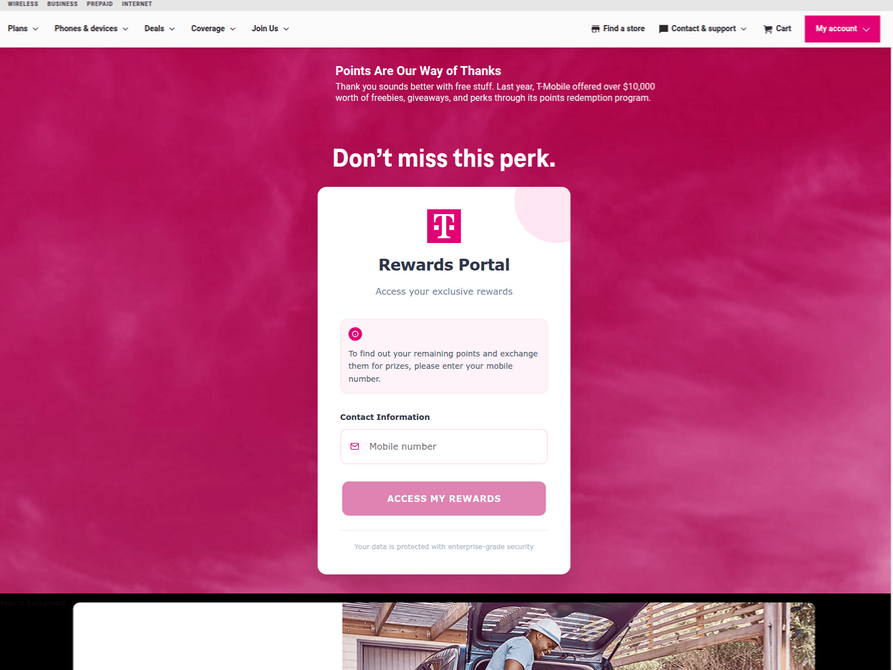
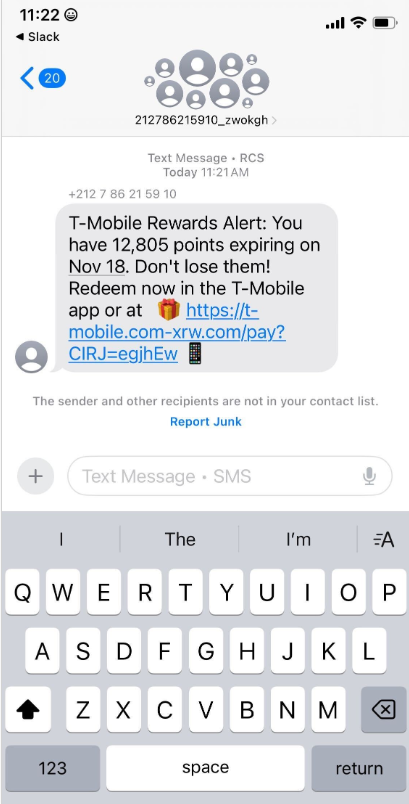
In a striking surge of activity over the past week, thousands of domain names have been registered for scam websites masquerading as legitimate offers. Specifically, many of these sites are enticing T-Mobile customers with the promise of claiming an abundance of rewards points. These deceptive domains are being actively promoted through scam messages delivered via Apple’s iMessage service and the functionally equivalent RCS messaging service integrated into Google phones. The malicious messages, often appearing as urgent notifications, create a sense of opportunity or urgency, prompting users to click through to the fraudulent websites.
The website scanning service urlscan.io has meticulously documented this alarming proliferation, showing that thousands of these phishing domains have been deployed in mere days. A critical vulnerability in this scam is its mobile-first approach; the phishing websites are designed to load exclusively when accessed via a mobile device. Once loaded, they aggressively solicit visitors’ personal information, including their full name, physical address, phone number, and crucially, their payment card details, all under the guise of facilitating the rewards point claim.
Upon submission of card data, the fraudulent sites escalate their deception by prompting the user to share a one-time code. This code, typically sent via SMS by the victim’s financial institution for legitimate transaction verification, is in reality being requested by the fraudsters who have just attempted to enroll the victim’s phished card details into an Apple or Google mobile wallet. If the victim, misled by the site’s claims of transaction verification, provides this one-time code, the phishers gain the ability to link the victim’s compromised card to a mobile device that they physically control. This grants them immediate access to funds and facilitates further fraudulent activities.
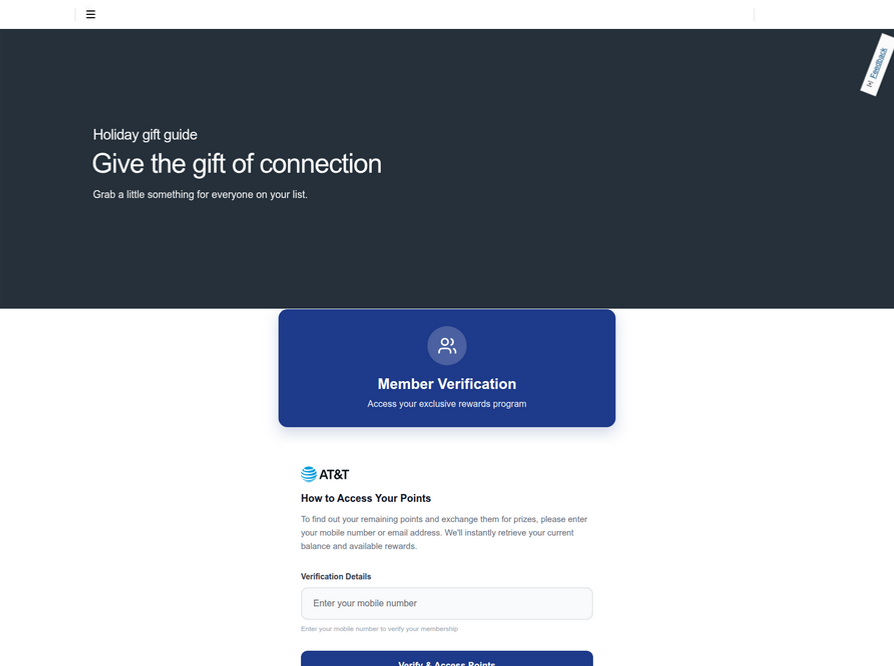
A deep dive into the domains identified by urlscan.io as being linked to this specific Chinese SMS phishing syndicate reveals a similar, alarming pattern targeting AT&T customers. This indicates a coordinated effort to exploit the customer bases of major telecommunication providers. Ford Merrill, a security researcher at SecAlliance, a CSIS Security Group company, elaborates on the origin and evolution of this threat. He notes that multiple China-based cybercriminal groups, operating under a "phishing-as-a-service" model, have been deploying these mobile points lures for some time. However, the recent escalation of this particular scam directly targeting consumers within the United States marks a significant shift in their operational focus.
Merrill points out that while these points redemption schemes have been prevalent in geographies like the EU and Asia for a considerable period, their recent surge in popularity within the U.S. consumer market is a cause for concern. The familiar tactic of spoofing telecommunication companies is just one facet of this evolving threat landscape.
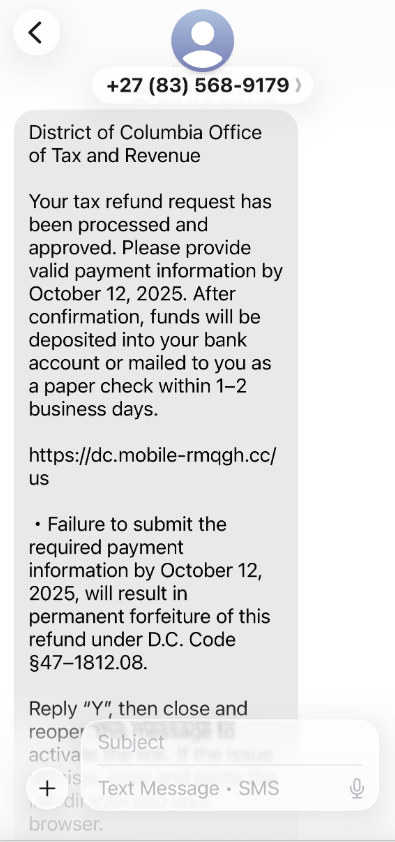
Further examination of domains flagged by urlscan.io as part of this Chinese SMS phishing syndicate reveals an even broader array of deceptive tactics. These groups are now actively spoofing U.S. state tax authorities, sending out messages that inform recipients they are eligible for an unclaimed tax refund. The underlying objective remains the same: to phish for the user’s payment card information and then trick them into divulging the one-time verification code.
CAVEAT EMPTOR
While many SMS phishing or "smishing" domains are rapidly identified and flagged as malicious by browser developers, a particularly concerning area of growth for these phishing kits lies in the creation of fake e-commerce shops. These fraudulent storefronts are far more insidious because they do not draw immediate attention through mass spamming campaigns. Instead, they operate with a more targeted and stealthy approach.
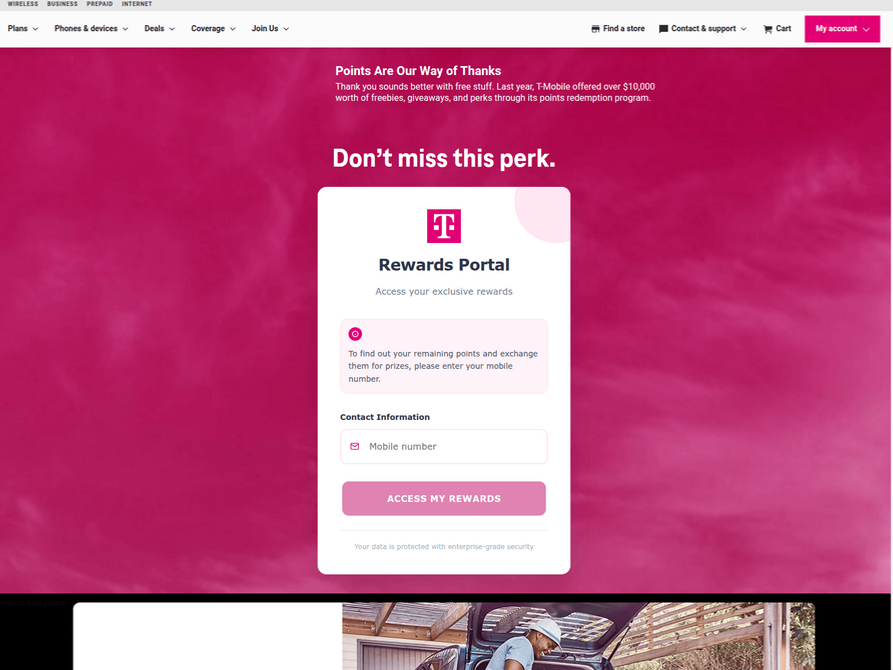
Merrill explains that the same Chinese phishing kits responsible for the ubiquitous package redelivery message scams are equipped with modules that enable the swift deployment of a multitude of fake, yet highly convincing, e-commerce storefronts. These phony stores are typically advertised on platforms like Google and Facebook. Consumers often stumble upon these sites when searching online for deals on specific products, falling victim to seemingly legitimate advertisements.
The modus operandi of these fake e-commerce stores is disturbingly effective. Customers, believing they are engaging in a standard online purchase, willingly supply their payment card and personal information during the checkout process. This is then followed by a request for a one-time code, purportedly from their financial institution to verify the transaction. In reality, this code is sent because the scammers are immediately attempting to enroll the supplied card data into a mobile wallet.
According to Merrill, the malicious code that identifies these sites as fraudulent is typically fetched only during the checkout process. This makes it exceptionally difficult to detect these stores through mass web scanning. Furthermore, the majority of customers who purchase items from these sites do not realize they have been defrauded until weeks later, when the anticipated items fail to arrive.
"The fake e-commerce sites are tough because a lot of them can fly under the radar," Merrill states. "They can go months without being shut down, they’re hard to discover, and they generally don’t get flagged by safe browsing tools." This prolonged period of undetected operation allows these phishing groups to accumulate substantial illicit gains before being identified and dismantled.
Fortunately, the reporting of these SMS phishing lures and their associated websites remains one of the most effective methods for their rapid identification and subsequent shutdown. Raymond Dijkxhoorn, CEO and a founding member of SURBL, a widely-used blocklist that flags domains and IP addresses associated with unsolicited messages, phishing, and malware distribution, highlights a crucial resource. SURBL has developed a website called smishreport.com, specifically designed to allow users to report any smishing messages they receive by forwarding a screenshot.
"If [a domain is] unlisted, we can find and add the new pattern and kill the rest" of the matching domains, Dijkxhoorn explains. "Just make a screenshot and upload. The tool does the rest." This crowdsourced approach to threat intelligence allows for the swift identification and mitigation of emerging phishing campaigns.
Merrill also notes a predictable seasonal surge in smishing activity. The final weeks of the calendar year typically witness a significant uptick in smishing attacks, particularly those impersonating the U.S. Postal Service or commercial shipping companies with package redelivery schemes.
"Every holiday season there is an explosion in smishing activity," he warns. "Everyone is in a bigger hurry, frantically shopping online, paying less attention than they should, and they’re just in a better mindset to get phished." The heightened sense of urgency and reduced vigilance during this period creates fertile ground for scammers to exploit.
SHOP ONLINE LIKE A SECURITY PRO
The prevailing strategy of simply purchasing from the online merchant offering the lowest advertised prices can, regrettably, resemble a game of Russian Roulette with one’s finances. Even consumers who primarily shop at well-established online retailers can fall victim if they are not vigilant against offers that appear too good to be true, especially when considering third-party sellers on these platforms.
For those encountering an unfamiliar online merchant, it is prudent to invest a few minutes in investigating their reputation. The risk of falling prey to a scam significantly increases when dealing with a brand-new online store. A simple yet effective method to gauge a site’s legitimacy is to perform a basic WHOIS search on its domain name. A recent "created" date for a site selling a highly sought-after gadget at an exceptionally low price is a strong indicator that it may be a phantom store.
When receiving a message that purports to warn of an issue with an order or shipment, it is paramount to navigate directly to the e-commerce or shipping website independently. Critically, avoid clicking on any links or opening attachments within such messages, particularly those that convey a sense of urgency or warn of dire consequences if immediate action is not taken. Phishers and malware distributors frequently exploit emergencies to create false alarms, often causing recipients to momentarily lower their guard.
However, it is not solely outright scammers who can derail holiday shopping endeavors. Often, items advertised at significantly discounted prices compared to other online stores may compensate by imposing exorbitant shipping and handling fees. Therefore, it is essential to scrutinize all terms and conditions before committing to a purchase.
Carefully review shipping timelines and ensure a clear understanding of the store’s return policies. Be vigilant for hidden surcharges and exercise caution when habitually clicking "ok" during the checkout process without full comprehension.
Most importantly, maintain a close watch on your monthly financial statements. Fraudsters often capitalize on the holiday season to embed unauthorized charges on stolen cards within the flurry of legitimate transactions. This makes it crucial to meticulously review your credit card bills and promptly dispute any charges that you did not authorize. Proactive vigilance and careful scrutiny of financial records are your strongest defenses against holiday-season fraud.