In a significant development that could reshape the landscape of cybercrime investigations, the operators of the notorious Kimwolf botnet, believed to have infected over two million devices, have seemingly gained unauthorized access to the control panel of Badbox 2.0, a massive botnet with deep roots in China and powered by malware pre-installed on numerous Android TV streaming boxes. This alleged breach, revealed through a leaked screenshot, provides a potential breakthrough for law enforcement agencies like the FBI and cybersecurity giants like Google, who have been actively pursuing the individuals behind Badbox 2.0. The bragging rights of the Kimwolf botmasters may have inadvertently handed investigators a crucial lead.
The Kimwolf botnet, first detailed in a January 2026 report titled "The Kimwolf Botnet is Stalking Your Local Network," has garnered attention for its highly invasive and disruptive propagation methods. The research highlighted that the vast majority of Kimwolf-infected systems were unofficial Android TV boxes, often marketed as a one-time purchase solution for unlimited, and often pirated, streaming content. This modus operandi preys on consumers seeking cost-effective entertainment, making these devices a prime target for malware.
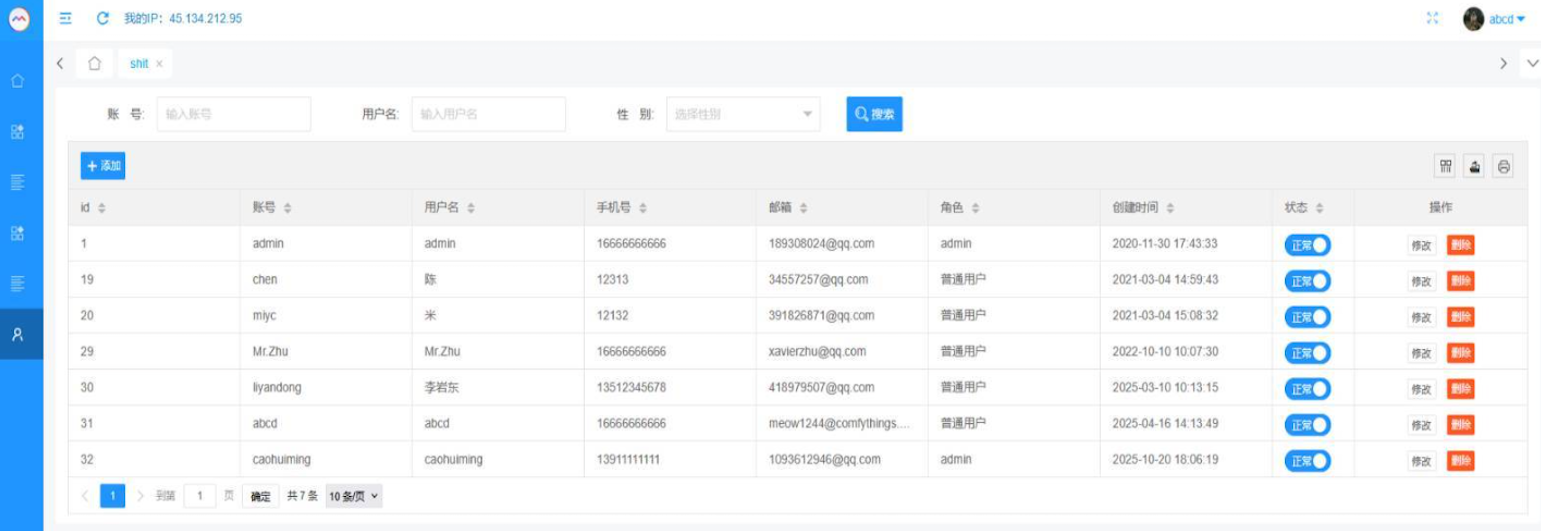
Further investigation into Kimwolf’s administration, published in the January 8, 2026, article "Who Benefitted from the Aisuru and Kimwolf Botnets?", identified the current administrators operating under the pseudonyms "Dort" and "Snow." The recent leak, purportedly from a former associate of Dort and Snow, showcases a screenshot taken by the Kimwolf operators while logged into the Badbox 2.0 botnet’s control panel. This image, partially displayed, lists seven authorized users, with one anomaly: the account "ABCD," which was logged in and prominently displayed in the top right of the screenshot, is reportedly controlled by Dort, who apparently managed to add their email address as a valid user to the Badbox 2.0 infrastructure.
The Badbox botnet boasts a long and concerning history, predating Kimwolf’s emergence in October 2025. In July 2025, Google initiated a "John Doe" lawsuit against 25 unidentified defendants, accusing them of operating Badbox 2.0. Google characterized it as a colossal botnet exceeding ten million unauthorized Android streaming devices, primarily engaged in advertising fraud. Their findings indicated that Badbox 2.0 compromised various device types even before purchase and could also infect devices through malicious apps downloaded from unofficial marketplaces.
This legal action followed closely on the heels of a June 2025 advisory from the Federal Bureau of Investigation (FBI). The FBI warned that cybercriminals were exploiting home networks by either pre-installing malware on devices before sale or by infecting them during the download of essential applications that contained backdoors, often during the initial setup process. The FBI’s discovery of Badbox 2.0 was a consequence of efforts to disrupt the original Badbox campaign, which was identified in 2023 and primarily targeted Android TV boxes compromised with backdoor malware before their sale.
Initially, KrebsOnSecurity expressed skepticism regarding the claim of the Kimwolf botmasters hacking into the Badbox 2.0 botnet. However, a deep dive into the history of the QQ.com email addresses visible in the leaked screenshot has lent significant credibility to the assertion.
CATHEAD
An online search for the email address [email protected], identified in the screenshot as belonging to a user named "Chen," reveals its association with several China-based technology companies. These include Beijing Hong Dake Wang Science & Technology Co Ltd., Beijing Hengchuang Vision Mobile Media Technology Co. Ltd., and Moxin Beijing Science and Technology Co. Ltd.
The website for Beijing Hong Dake Wang Science, asmeisvip[.]net, was flagged in a March 2025 report by HUMAN Security as one of many sites involved in the distribution and management of the Badbox 2.0 botnet. Similarly, moyix[.]com, linked to Beijing Hengchuang Vision Mobile, is also implicated.
Data from the breach tracking service Constella Intelligence indicates that [email protected] once used the password "cdh76111." A deeper analysis of this password within Constella’s database shows it was also utilized by two other email accounts: [email protected] and [email protected].
Constella’s records reveal that [email protected] registered an account on JD.com, China’s largest online retailer, in 2021 under the name "陈大海," which translates to "Chen Daihai." DomainTools.com further corroborates this connection, showing Chen Daihai’s name in the original registration records (dating back to 2008) for moyix[.]com, along with the email address cathead@astrolink[.]cn.
Notably, astrolink[.]cn is also among the domains identified as part of the Badbox 2.0 infrastructure in HUMAN Security’s 2025 report. DomainTools further links cathead@astrolink[.]cn to the registration of over a dozen domains, including vmud[.]net, another domain identified by HUMAN Security as being associated with Badbox 2.0.
XAVIER
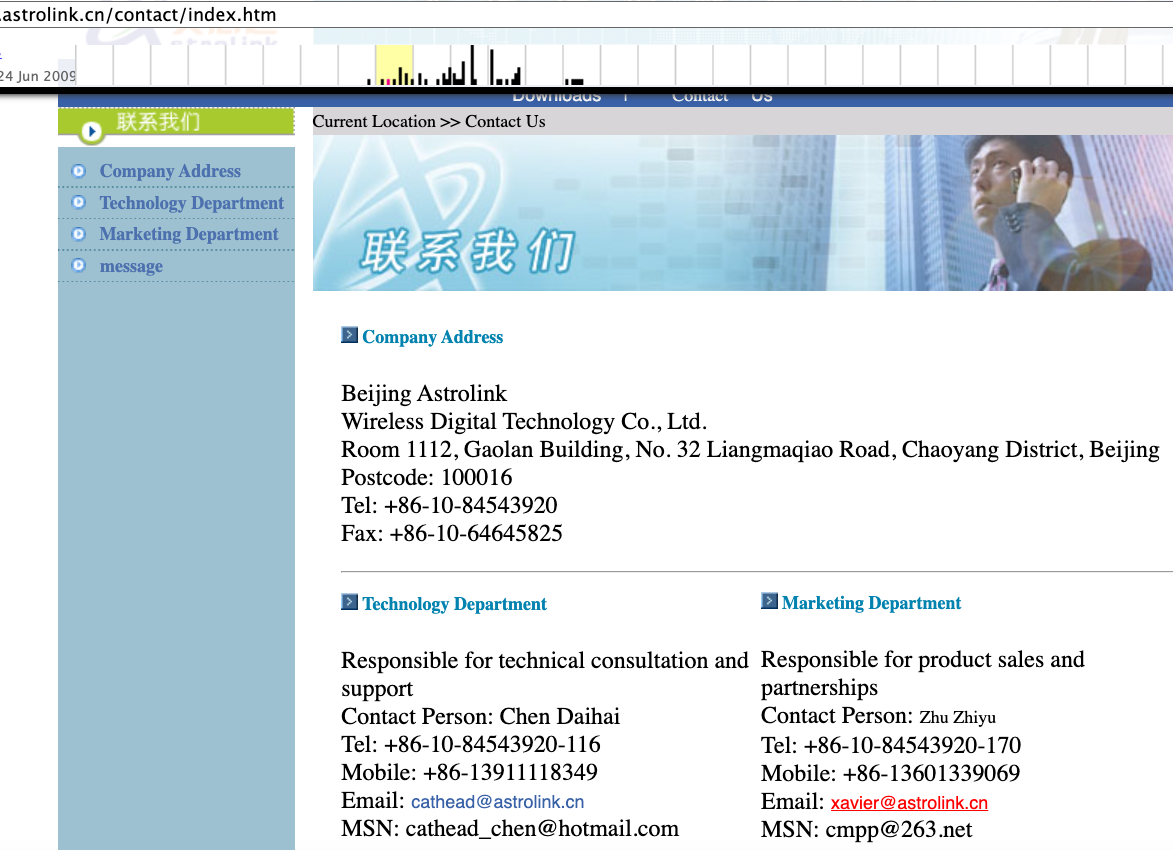
A cached version of astrolink[.]cn from archive.org reveals it belongs to a mobile app development company named Beijing Astrolink Wireless Digital Technology Co. Ltd. An archived "Contact Us" page from around 2007 lists Chen Daihai as a member of the company’s technology department. The other individual featured on that page is Zhu Zhiyu, with the email address xavier@astrolink[.]cn.
This connection becomes more significant when considering the Badbox 2.0 panel, where a user identified as "Mr.Zhu" used the email address [email protected]. Constella’s search of this address reveals a JD.com account registered under the name Zhu Zhiyu. A distinctive password used for this account matches that of [email protected]. DomainTools identifies [email protected] as the original registrant of astrolink[.]cn.
ADMIN
The earliest listed account in the Badbox 2.0 panel, "admin," registered in November 2020, utilized the email address [email protected]. DomainTools links this email to the 2022 registration records for the domain guilincloud[.]cn, which lists the registrant name as "Huang Guilin."
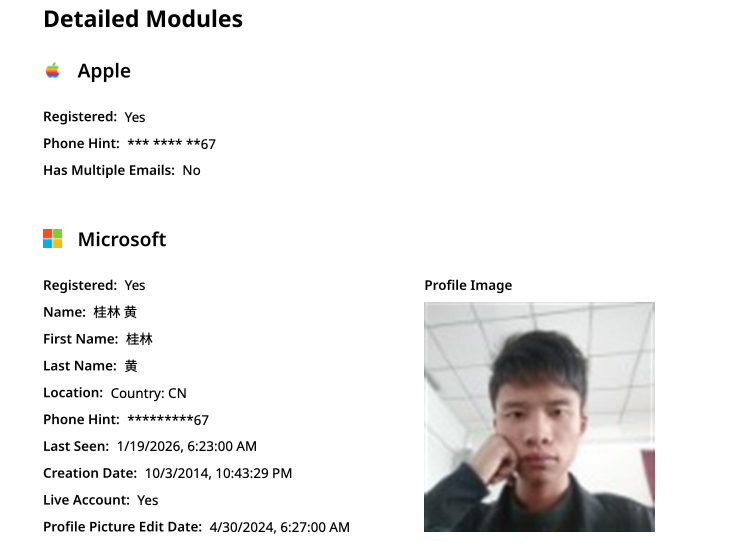
Constella Intelligence finds that [email protected] is associated with the Chinese phone number 18681627767. Open-source intelligence platform osint.industries reveals that this phone number is linked to a Microsoft profile created in 2014 under the name Guilin Huang (黄桂林). Cybersecurity intelligence platform Spycloud reports that this phone number was used in 2017 to create a Weibo account under the username "h_guilin."
The remaining three users and their corresponding QQ.com email addresses in the Badbox 2.0 panel were also connected to individuals in China. However, no apparent links were found between these individuals, nor Mr. Huang, and the entities established and operated by Chen Daihai and Zhu Zhiyu, or any other corporate structures. Attempts to solicit comments from these individuals were unsuccessful.
A comprehensive mind map, detailing search pivots on email addresses, company names, and phone numbers, strongly suggests a connection between Chen Daihai, Zhu Zhiyu, and the Badbox 2.0 botnet.
UNAUTHORIZED ACCESS
The possibility of Kimwolf operators directly accessing the Badbox 2.0 botnet is a significant development, primarily due to Kimwolf’s unique propagation methods. The Kimwolf botmasters discovered a way to leverage residential proxy services to relay malicious commands to vulnerable devices within the local networks of unsuspecting users, bypassing their firewalls.
These vulnerable systems are predominantly Internet of Things (IoT) devices, such as unofficial Android TV boxes and digital photo frames, which often lack basic security features or authentication mechanisms. In essence, any device that can be communicated with can be compromised with a single command.
Previous research from the proxy-tracking firm Synthient, highlighted in a January 2026 report, alerted 11 residential proxy providers to the vulnerability of their endpoints, which were being abused for local network probing and exploitation. Many of these providers have since implemented measures to prevent such upstream network access, seemingly hindering Kimwolf’s rapid expansion.
However, the source of the Badbox 2.0 screenshot claims the Kimwolf botmasters possessed an alternative strategy: covert access to the Badbox 2.0 botnet control panel. "Dort has gotten unauthorized access," the source stated. "So, what happened is normal proxy providers patched this. But Badbox doesn’t sell proxies by itself, so it’s not patched. And as long as Dort has access to Badbox, they would be able to load the Kimwolf malware directly onto TV boxes associated with Badbox 2.0."
The exact method by which Dort gained access to the Badbox botnet panel remains unclear. Nevertheless, it is highly probable that Dort’s unauthorized account will not remain operational for long. Following notifications sent to the QQ.com email addresses listed in the control panel screenshot, including a copy of the image and inquiries about the anomalous "ABCD" account, the situation is likely to evolve rapidly. This alleged intrusion into Badbox 2.0 by Kimwolf operators could provide a critical pathway for law enforcement to identify and apprehend the masterminds behind both formidable botnets.