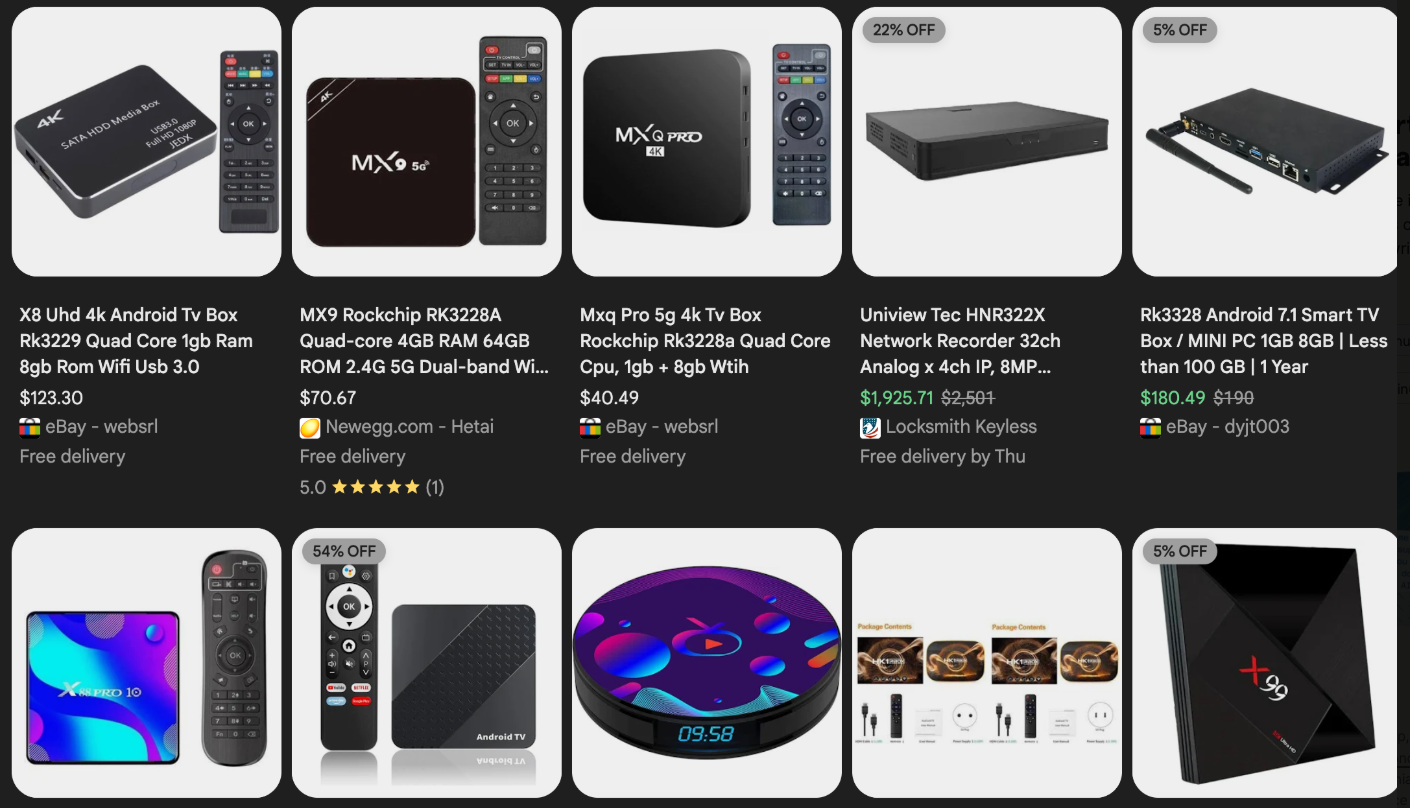
These residential proxy networks, often advertised as tools for anonymizing or geo-locating internet traffic, are typically bundled with untrustworthy mobile applications and games. A significant vector for Kimwolf’s infection, however, originates from unofficial Android TV boxes readily available on major e-commerce platforms like Amazon, BestBuy, Newegg, and Walmart. These devices, priced between $40 and $400 and marketed under a bewildering array of obscure brands, frequently entice consumers with the promise of free, pirated subscription video content. Yet, the hidden cost of this illicit streaming is the transformation of these devices into entry points for Kimwolf. Synthient, a security firm tracking the botnet, has identified that a staggering two-thirds of Kimwolf infections are linked to these Android TV boxes, which often lack any built-in security or authentication mechanisms, leaving them wide open to compromise. The threat extends beyond TV boxes, with Kimwolf also adept at infecting Internet-connected digital photo frames, particularly those running the Uhale app, which has been found to have critical security flaws. Amazon’s bestselling digital frame as of March 2025 was identified as a vulnerable target.

The fundamental security flaws in these devices and unauthorized TV boxes are twofold. Firstly, a substantial number come with pre-installed malware or necessitate the download of unofficial Android apps, often leading to the installation of programs that turn the device into a residential proxy node. Secondly, and perhaps more critically, these devices rely on microcomputer boards with no inherent security or authentication. This means that any device on the same local network can potentially be compromised with a single command, creating a domino effect of infection.
The alarming confluence of these vulnerabilities came to light through the diligent work of Benjamin Brundage, a 22-year-old computer science student at the Rochester Institute of Technology and founder of the cybersecurity firm Synthient. Brundage’s research, conducted while he was preparing for final exams, indicated that Kimwolf was an Android-based variant of the Aisuru botnet. His investigation revealed that Kimwolf’s rapid proliferation was fueled by a critical flaw in many of the world’s largest residential proxy services. These services, he explained, were failing to adequately prevent their clients from initiating requests into the internal networks of proxy endpoints. While most proxy services implement basic safeguards, such as blocking requests to RFC-1918 private IP address ranges (10.0.0.0/8, 192.168.0.0/16, and 172.16.0.0/12), the architects of Kimwolf discovered a method to circumvent these restrictions. By manipulating Domain Name System (DNS) settings to point to these internal address ranges, they could directly communicate with devices on local networks. Brundage’s critical advisory, sent to nearly a dozen residential proxy providers in December 2025, warned that this vulnerability was actively being exploited to distribute malware.
The insidious nature of these attacks is further amplified by the fact that many residential proxy services operate on mobile devices, often embedded within seemingly innocuous apps, turning user phones into proxy nodes without explicit consent. Synthient’s recent report highlights that Kimwolf operators are actively monetizing their botnet through app installs, the sale of proxy bandwidth, and the provision of DDoS attack capabilities, underscoring a growing trend of threat actors leveraging unsecured proxy networks for various malicious purposes.
Adding another layer to the Kimwolf threat is the widespread default enablement of Android Debug Bridge (ADB) mode on many unofficial Android TV boxes. ADB, a powerful diagnostic tool intended for manufacturing and testing, allows for remote configuration and firmware updates. However, when left enabled, it creates a critical security vulnerability by constantly listening for and accepting unauthenticated connection requests. A simple command like "adb connect [device’s local IP address]:5555" can grant unrestricted administrative access, a backdoor that Kimwolf actively exploits. Brundage’s investigation revealed a direct correlation between new Kimwolf infections and proxy IP addresses offered by IPIDEA, identified as the world’s largest residential proxy network. He observed Kimwolf rapidly expanding by exploiting IPIDEA’s proxy pool, demonstrating its ability to rebuild itself from near-zero to millions of infected systems within days by tunneling through these compromised endpoints. Synthient’s analysis of IPIDEA’s proxy pool revealed that over two-thirds of the exposed devices were Android-based and lacked any authentication, making them easy targets.
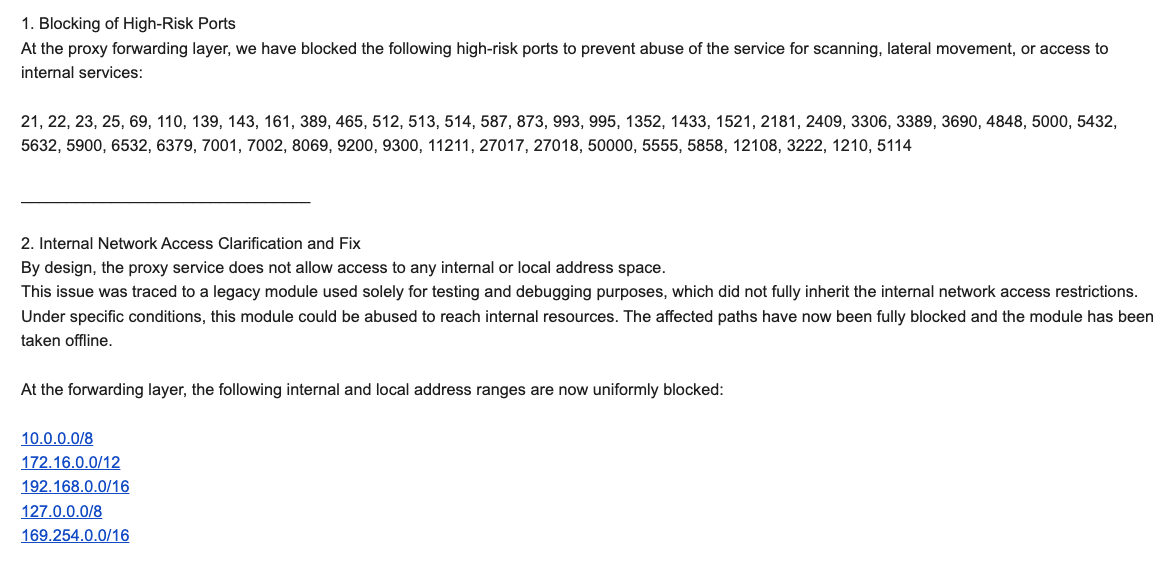
Following his discovery, Brundage meticulously documented his findings and on December 17, 2025, he issued a security notification to 11 affected proxy providers, including resellers of IPIDEA’s service, providing them with a window to address the vulnerabilities. While IPIDEA initially denied any association with the Aisuru botnet, their security officer, Byron, later acknowledged a vulnerability in a legacy testing module that allowed for internal network access. IPIDEA claimed to have patched this issue, implemented DNS resolution blocks for internal IP ranges, and begun blocking traffic on high-risk ports. Brundage confirmed that IPIDEA appeared to have successfully remediated the identified vulnerabilities, noting that he had not observed Kimwolf actors targeting other proxy services. Riley Kilmer, founder of Spur.us, a firm specializing in proxy traffic detection, corroborated Brundage’s findings, confirming that IPIDEA and its affiliates provided unfiltered access to local area networks (LANs). Kilmer specifically pointed to the Superbox, a popular unauthorized Android TV box, which leaves ADB running on localhost:5555, creating a direct pathway for attackers to install malicious software via an IPIDEA proxy.
The lineage of IPIDEA is further linked to the notorious 911S5 Proxy, a service that operated from 2014 to 2022 and was known for its widespread abuse on cybercrime forums. 911S5 imploded shortly after KrebsOnSecurity published a detailed investigation into its origins, with its operators claiming a data breach. The U.S. Treasury and Department of Justice later sanctioned and arrested individuals associated with 911S5. Kilmer suggests that IPIDEA, along with its sister service 922 Proxy, is a direct successor, actively seeking to attract 911S5’s former clientele. Oxylabs, another proxy provider that received Synthient’s notification, confirmed implementing security changes to prevent bypasses to private network addresses but stated there was no evidence of Kimwolf exploiting their network.
The practical implications of the Kimwolf botnet are profound, transforming seemingly innocuous Wi-Fi sharing into a potential vector for infection. If a guest connects an infected device to your network, their public IP address can be leveraged by attackers to tunnel into your local network, scanning for vulnerable devices like digital photo frames and unauthorized Android TV boxes with ADB enabled. This could result in your own devices becoming infected, even if you never intended for them to be exposed to the internet. Furthermore, attackers could potentially manipulate your router’s DNS settings to redirect your web traffic to malicious servers, reminiscent of the 2012 DNSChanger malware.
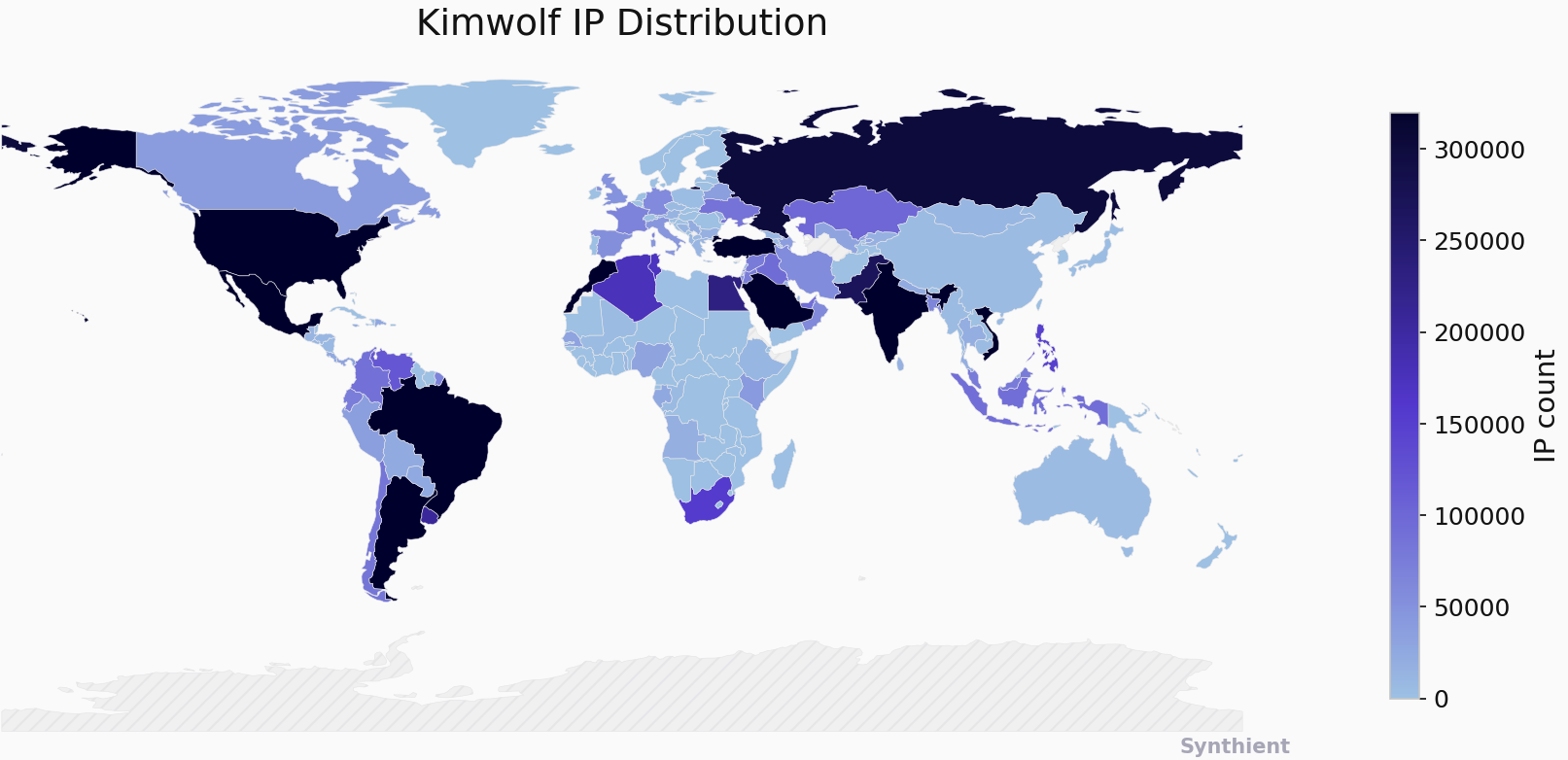
The Chinese security firm XLab has also been instrumental in chronicling Kimwolf’s rise, identifying its control servers and observing its rapid growth. XLab’s research suggests that Kimwolf has enslaved between 1.8 and 2 million devices, with significant concentrations in Brazil, India, the United States, and Argentina. They noted that accurately measuring the botnet’s scale is challenging due to dynamic IP allocation and varying online times of infected devices across global time zones. Intriguingly, XLab observed an almost "obsessive" fixation by the Kimwolf author on this publication, with "easter eggs" related to the author’s name embedded within the botnet’s code and communications.
Identifying Kimwolf infections or pre-existing residential proxy malware on a local network is a significant challenge for the average user, as it requires specialized tools and technical expertise. Synthient has provided a helpful resource on its website where users can check if their public IP address has been identified as part of a Kimwolf-infected system. They have also compiled a list of the most prevalent unofficial Android TV boxes involved in the botnet. Owners of these devices are strongly advised to disconnect them from their networks immediately. Chad Seaman of Akamai Technologies urges consumers to be highly skeptical of cheap, unofficial devices and residential proxy schemes, emphasizing that the notion of a secure local area network is now outdated. He warns that malicious applications can compromise not only Android devices but also Macs, Windows PCs, and iPhones, potentially opening networks to widespread unauthorized access.
The threat posed by these devices is further underscored by Google’s lawsuit against the "BadBox 2.0 Enterprise" botnet, comprising over ten million unauthorized Android streaming devices engaged in advertising fraud. This lawsuit followed a June 2025 advisory from the FBI, which warned of cybercriminals gaining unauthorized access to home networks by pre-installing malware or infecting devices during setup. Lindsay Kaye of HUMAN Security, a firm involved in the BADBOX investigations, highlighted that these botnets and their associated residential proxy networks were detected due to their significant role in advertising fraud, ticket scalping, retail fraud, account takeovers, and content scraping. Kaye advises consumers to stick to reputable brands for connected devices and to be cautious about app installations. Implementing a "Guest" Wi-Fi network on routers can also provide a safer browsing experience for visitors, isolating their devices from the main local network. While some argue that these devices can be "flashed" with custom firmware, the majority of purchasers are not security experts and are often unaware of the risks associated with these devices, which are largely marketed for video piracy and lack basic security features, making them attractive targets for cybercriminals. The entertainment industry’s relative inaction in pressuring e-commerce vendors to cease the sale of such malicious hardware remains a point of concern.

Part II of this series will delve deeper into the clues left behind by the apparent architects and beneficiaries of the Kimwolf botnet.